
- What is Information Security Assurance?
It is the management and protection of knowledge, information, and data. It combines two fields: Information assurance, which focusing on assuring the availability, integrity, authentication, confidentially, and non-repudiation of information and system.
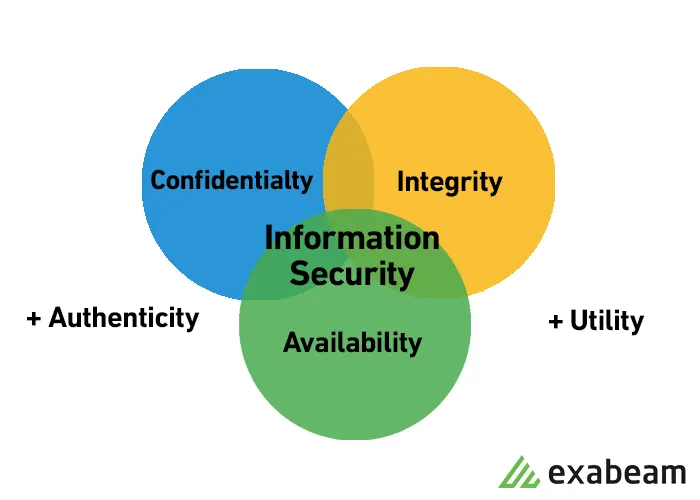
-Components information security assurance.
The basic components of information security assurance are most often summed up by the so-called CIA triad: confidentiality is perhaps the elements of the triad that most immediately comes in to the mind when you think of information security.

-Differentiate the certification programs to the common body language.
Body language designed to help you understand the different aspects of body language so that you are able to use the information to your personal and professional advantage while certification program is a defined set of components or training programs offered by your organization to members to prove that they have achieved measured level of knowledge within the designated timeline.

-Differentiate the governance and risk management.
Governance or corporate governance is the overall system of rules, practices, and standards that guide a business. Risk or enterprise risk management, is the process of identifying potential hazards to business and acting to reduce or eliminate thier financial impact.
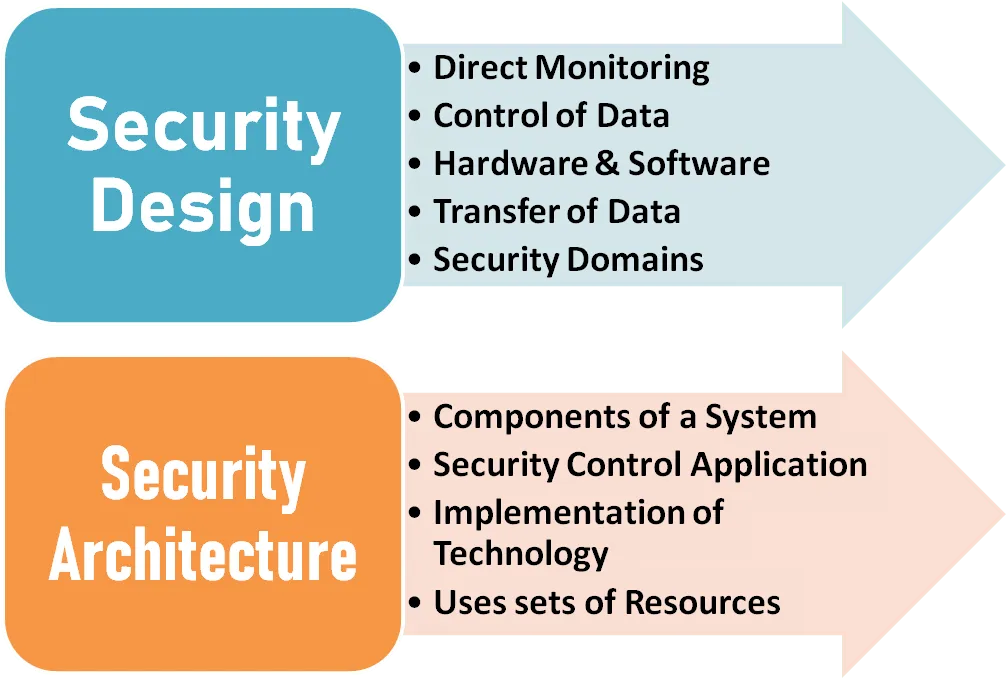
-Different between security architecture to design.
Security architecture and design looks at how information security controls and safeguard are implemented in IT systems in order to confidentiality, integrity, and availability of the data that are used, processed, and stored in those systems.
-Different between business continuity planning to disaster recovery planning .
Business continuity focuses on keeping business operational during a disaster, while disaster recovery focuses on restoring data access and IT infrastructure after a disaster.
Meanwhile, a disaster recovery strategy helps to ensure an organization's ability to return to full functionality after a disaster occurs.

-What is physical security control?
Physical control is the implementation of security measures in a defined structure use to deter or prevent unauthorized access to sensitive material. Examples of physical control are: closed-circuit surveillance cameras, motion or thermal alarm systems, security guards.

-What is operations security?
Operations security or OPSEC is a security and risk management process that prevents sensitive information from getting into the wrong hands. OPSEC is both the process and a strategy, and it encourages IT and security managers to view thier operations and system from perspective of a potential attacker.

-What is law?
The systems of rules which a particular country or community recognizes as regulating the actions of it's members and which it may enforce by the imposition of penalties.

-What is investigation?
The action of investigating of something or someone. Formal or systematic examination or research. A formal inquiry or systematic study.

-What is ethics?
Moral principles that govern a person's behavior or the conducting of an activity. The branch of knowledge that deals with principles.

-What is information security?
The state of being protected against the unauthorized use of information, especially electronic data, or the measures taken to achieve
this.