This is the 5th post of a series for teaching cyber-security in a coding-club. Read [part 4]
Listing hidden files
The ls command ommited directories and files with a dot
Aha! You are becoming a sharp-eyed developer.
If you enable "show hidden files" in your folder, you will see some additional files. There are some files and directories that start with a dot that are not being printed by the ls command, why is that?
Hidden files and hidden directories
Dotfiles as they are usually known, are commonly used for storing user preferences or user configuration.
The intention of files or folders that start with a dot character is simply to not "clutter" the display of the contents of a directory listing with files the user did not directly create or wants to remain hidden from casual inspection.
So can we list hidden files and folders?
Yes, we can!
- Click on the terminal window
- Type:
ls -a - Press the return key
In addition to the ls command, we are typing 2 characters more: -a, this set of characters are called: command options.
What does the -a character do
Executing the ls command outputs only the visible files on our current directory, however, hidden files are very important for security. They often contain important information about who is allowed where and where passwords are stored.
Introducing: command options
After executing the ls -a command, we’ve got a larger output:
codio ~/workspace $ ls -a
. .. dir1 empty-file.txt .git .gitignore .guides
If you use this course, you will need to create some hidden files for your students.
Can you recognize the hidden vs. the normal files and folders?
Command options
Bash commands accept options after the command name. These options complement the command output by adding or structuring information regarding the text, file or directory over which the command is acting upon.
Command options are written after the command name and begin with a - symbol followed by the option character. For example, we did ls -a which means list files -all or in other words show me all files in this directory.
Wonder what all of those dots, double dots and other hidden files and directories mean?
Why are there dots without a name after them?
Take a closer look at the ls -a output listing our current directory contents.
Can you guess which are files and which are directories?:
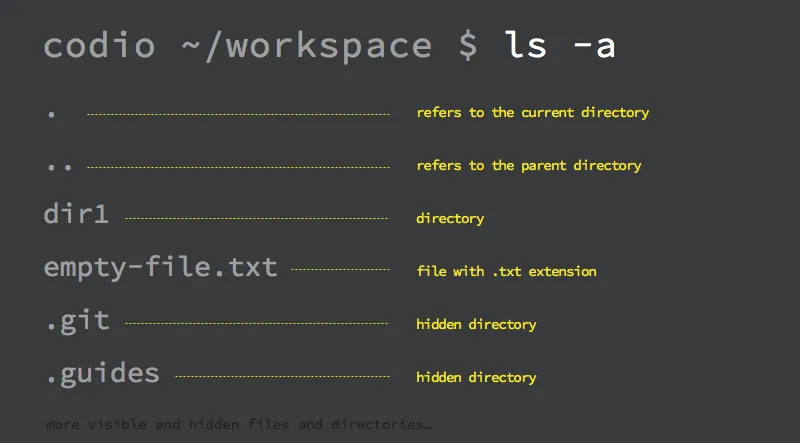
source: codio.com
As you can see, bash sorts files and directories alphabetically starting with the dots.
 Single and double dots
Single and double dots
Dots in bash are useful utilities that help on navigating the file system using the CLI.
In an ls listing
.refers to the current directory, more on this later..refers to the parent directory, the directory immediately above the current directory. We'll apply this knowledge later. Continue reading [Part 6]