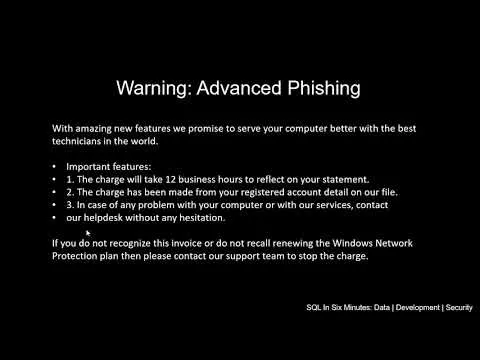
One popular myth we hear a lot on corporate and college courses on phishing is that there are certain patterns with phishing emails that allow us to know we're being phished. Some of these patterns involve poor English, a link in the email to do some action on our accounts, illegitimate domains, and a few other signs. In addition, we often hear promises of better security thanks to artificial intelligence that can spot these emails and protect our inboxes because they recognize these patterns. These courses can actually do more harm than good as sophisticated phishers can do the opposite of these signs and appear to be legitimate. In the video, Advanced Phishing Email - When Protective AI May Harm, I cover an example of a superior phishing email that uses some techniques that I've been warning consumers about for a while - one of which is social media.
Some important points and questions that are addressed in this video that you should consider with security and email:
- What are some popular myths about phishing in the security community that could potentially harm users?
- What is a tool that some email providers have that can possibly get you in trouble or possibly assist hackers with better phishing?
- Why should we be extremely careful with blanket rules about security? What's a statistical reason that this could potentially harm our security in the future?
- After reviewing the video, what is one very dangerous part of the email that was received that could potentially fool many people because it's so common in other phishing emails, yet not in this one?
- What social network actually helped this phishing attempt and how could this backfire when someone researches the person? Note that backfire in this case isn't just a compromise, it also involves the person on LinkedIn being thrown under the bus as a part of this spoofing attempt.
- How does this email provide an example of what I've been warning about related to social media as far as compromising security?
For mastering data transformation from one form to another form, check out the highest-rated Automating ETL course on Udemy. For a coupon to the course, check out the trailer video on the channel SQL In Six Minutes.
The irony of many of these courses and training is that they've created false security. By telling people to look for warning signs, some people will think an email like the above is safe. It's not. It's actually very dangerous. I predict that quite a few people will be thrown off by it. Unfortunately, this is one of the complexities of security: hackers can often be more sophisticated than we want to consider. Another problem is that corporate environments often "test" their users by sending phishing emails that actually are poorly designed. The intention is good - "we're training our employees against phishing." But advanced phishing is not tested and therefore may end up hurting employees because they receive what appears to be a legitimate email. Or they receive this in a personal account and they open it at work (disturbing, but some people use their work computer to check personal email - very poor security, but this is allowed in some companies).
We all love to over simplify things because the digital world is more complex than many of us understand (I include myself in this). This complexity means we want quick rules to obey. But complexity means that techniques change in time and hackers can switch up what they're doing to compromise us in the future. Unfortunately, the rules of yesterday are not the rules of today and won't be the rules of tomorrow. Advanced hackers have gotten much better at their phishing techniques and this will continue. Just like there are no links in the emails of today, there may not even be contact information in the emails of tomorrow - they'll have new tactics for compromise.
As we see in the above topic, security will continue to become a concern as people rush into the digital world without consideration of the consequences. I highly recommend the full Security playlist on my channel and some videos I especially suggest are:
- What is linkability?
- Who are hackers and why do they hack?
- Why is everyone freaking out about intellectual property theft?
Are you considering a design that involves storing significant personal information? Given the increase in attacks and leaks with personal data, you would be best to avoid this. But this will involve creativity and re-considering how you develop an idea that succeeds. For alternative designs that are profitable, you can get in touch and we'll review your idea and how it can be architected to protect your customers, while also protecting your company from future liability. You can contact for assistance.