
Email is now a vital part of both our professional and personal lives. We use it for everything from sharing photos with family to sending confidential business documents. But have you ever thought about how safe your emails really are? The thing is, standard email is often sent in plain text, which makes it susceptible to interception and unauthorised access. That's where email encryption comes in.
Encrypting emails means making them unreadable by anyone other than the people you're sending them to. It basically takes your readable message, or plaintext, and turns it into an unreadable, scrambled format called ciphertext. Only someone with the right decryption key can convert the ciphertext back into plaintext. This process is really important for protecting sensitive information like personally identifiable information (PII), financial data, legal contracts, or intellectual property from cybercriminals.
How Encryption Works
Encrypting emails basically means using cryptographic algorithms and keys. These keys are basically a string of bits that are essential for scrambling and unscrambling data. There are two main types of encryption: symmetric and asymmetric.
Symmetric-key encryption uses a single, shared key for both encrypting and decrypting data. It's fast and efficient, but the main challenge lies in securely sharing the secret key with the recipient. If the key is intercepted, the entire communication is compromised.
Asymmetric-key encryption, also known as public-key cryptography, is more complex but more secure for key distribution. It uses a pair of mathematically linked keys: a public key and a private key. The public key can be shared with anyone and is used to encrypt a message. The private key, however, is kept secret by the recipient and is the only key that can decrypt a message encrypted with its corresponding public key.
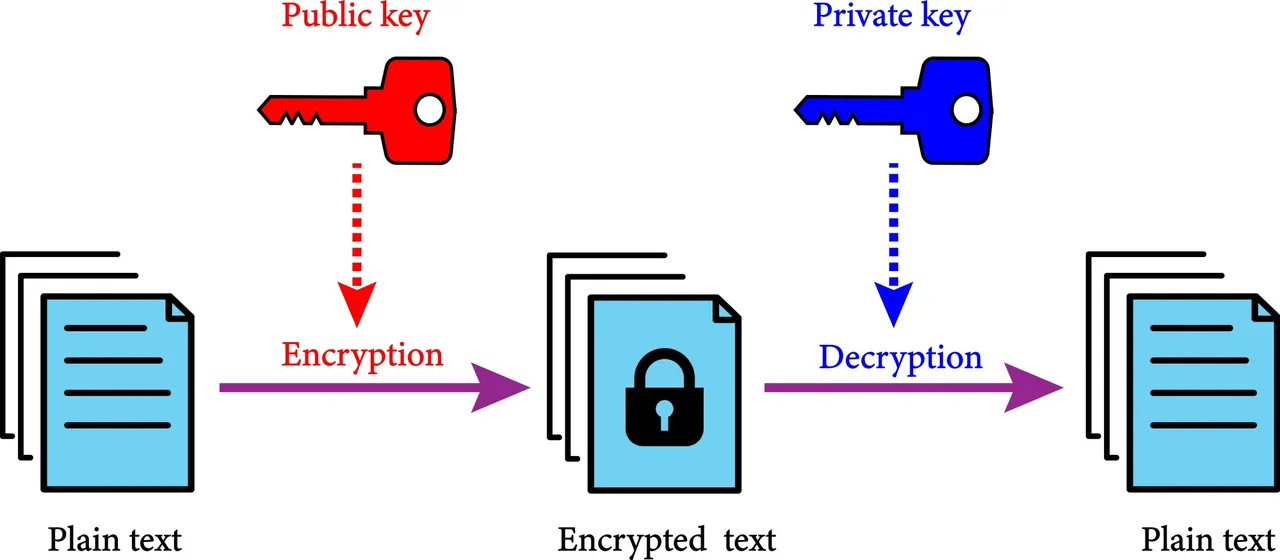
This means you don't need to worry about securely sharing a secret key, because the public key is public by design.
Most modern email encryption protocols use a hybrid approach that combines both symmetric and asymmetric methods. The sender uses the recipient's public key to encrypt a temporary, randomly generated symmetric key. Then, the actual email content is encrypted with this symmetric key, which is faster for large amounts of data. The person receiving the message uses their private key to decrypt the temporary symmetric key, and then uses that key to decrypt the message content.
Understanding the Main Encryption Methods
When we talk about encrypting email, we're typically referring to two main types of protection: transport encryption and end-to-end encryption.
Transport Layer Security (TLS): This is the most common form of encryption used by major email providers like Gmail, Outlook, and Yahoo. TLS encrypts the connection between your email client and the server, and also between email servers as the message is in transit. While this prevents most "man-in-the-middle" attacks, it doesn't protect the message once it arrives at the server. The email provider can still access the message in plaintext. It's a bit like sending a letter in a locked truck, but the post office staff can open the truck, read the letter, and then put it in another locked truck for the next leg of its journey.
End-to-End Encryption (E2EE): This is the gold standard for email security. E2EE ensures that the message is encrypted on the sender's device and can only be decrypted by the recipient's device. Intermediaries, including the email provider, cannot access the plaintext message. This is like putting the letter in a locked box that only the recipient has the key to. The post office can't open it, no matter what. To achieve this level of security, you need to use a protocol that supports E2EE, such as S/MIME or PGP.
The Most Seamless Way to Encrypt Email
While setting up S/MIME or PGP manually can give you strong security, it often needs some technical know-how and can be a big obstacle for many users. If you want to get true end-to-end encryption, the easiest way is to use a dedicated encrypted email service. These services handle all the cryptographic complexities in the background, making the process virtually effortless for the user.
These services are built from the ground up with privacy and security in mind. They usually use a version of E2EE (often a tweaked version of PGP) and handle the key exchange and decryption process automatically within their ecosystem. This means you can send encrypted emails to other users of the same service without having to do any manual configuration. If you need to send an encrypted email to someone on a different service, they often provide a secure link to a web portal where the recipient can access the message after entering a pre-shared password. A great example of such an encrypted email service is Atomic Mail.
These services are an excellent option for anyone who wants strong email security without the headache of manual setup. They represent the most accessible path to protecting your digital communications.
Practical Steps for Encrypting Your Emails
While moving to a new service is the most straightforward, you might need to encrypt emails within your existing provider. Here's how you can do it, depending on your setup.
For Enterprise Users (S/MIME)
If your organization uses a platform like Microsoft 365 or Google Workspace, your IT administrator may have already enabled S/MIME.
Obtain a Certificate: Your first step is to get a digital certificate, which may be provided by your company or a third-party Certificate Authority.
Configure Your Client: In Outlook, for example, you would go to File > Options > Trust Center > Trust Center Settings > Email Security. Here, you can import your certificate and configure the settings to encrypt messages by default or on a per-message basis.
Send an Encrypted Email: When composing a new email, look for an Encrypt button or an option under the Options tab. If S/MIME is configured correctly, the email client will automatically encrypt the message if the recipient's public key is available.
For Advanced Users (PGP)
For those who need PGP, the process is a bit more manual.
Install a PGP Client: You'll need to install a PGP software suite like GnuPG (GPG). This is the command-line backbone for many PGP solutions.
Generate a Key Pair: Use GPG to generate your public and private key pair. You'll be asked to provide your name, email, and a strong passphrase to protect your private key.
Share Your Public Key: Share your public key with anyone you want to communicate with. You can upload it to a public key server or send it as an attachment in an unencrypted email. You'll also need to get the public keys of your recipients.
Install a Plugin: Use a mail client that supports PGP integration or a browser extension for webmail. You can then encrypt and decrypt messages directly within your email interface.
Conclusion
These days, with data breaches and digital surveillance being so common, email encryption isn't just for people who are really into security. It's a really important tool for protecting your privacy and sensitive information. While S/MIME and PGP are great for security, they can be a bit tricky to get the hang of. Most users find that the best option is to switch to a dedicated encrypted email service. These platforms make strong encryption available to everyone, which is really important in today's digital world.