John McAfee is one of the more bombastic and eccentric personalities in the crypto space. Besides making a wager to eat his own member based on a Bitcoin price prediction, he has also gained a lot of what the kids call "clout" for this video regarding the AntiVirus software he created. (Among other things)

He can be entertaining. I'll grant him that.
He has recently been pushing a peculiar notion. This idea that data encryption is ultimately futile.
The below tweet isn't the "meat and potatoes" of this discussion. Thought it fit the form of tweets that one may find on the /r/ihadastroke subreddit which I find amusing.
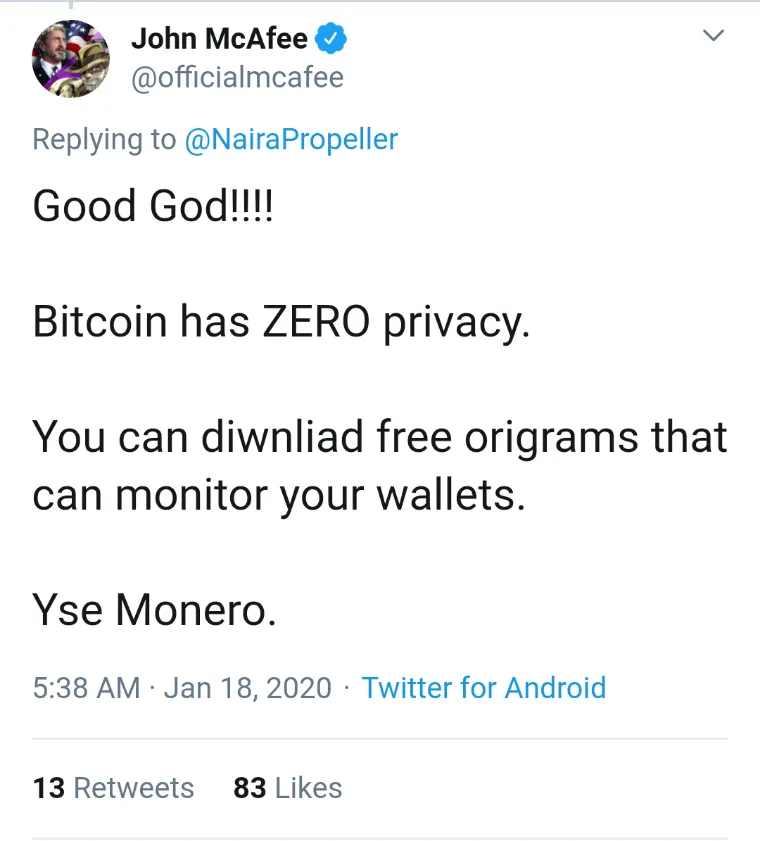
𝐂𝐮𝐫𝐬𝐞 𝐭𝐡𝐨𝐬𝐞 𝐩𝐞𝐬𝐤𝐲 𝐨𝐫𝐢𝐠𝐫𝐚𝐦𝐬!
It's not difficult to ascertain what he's trying to say here but looks like he may have had a mini stroke trying to type it. The tweet that had started it all is linked in the below image.
Decided a bit of clarification was in order
Being an industry certified information security professional with over a decade of experience in my field, I decided to engage him on this topic. The results were not what I had anticipated.
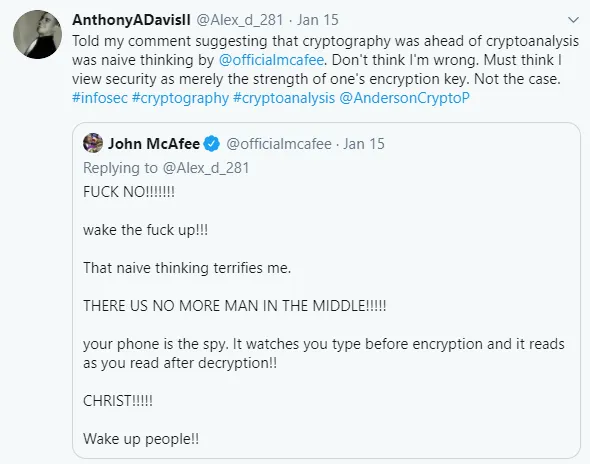
What I found disturbing is the overarching idea that he is trying to push that MITM (Man-in-the-Middle) cyber attacks are not a thing.
The implicit premise of the claim is ALL conceivable devices we could own are already compromised. From single board computer, smartphones, IoT devices, tablets to beefy gaming desktops, that is BOLD claim to make.
The conclusion that he makes is that encryption is now useless is quite frankly ludicrous!

Cocaine is a helluva drug.
This is a potentially dangerous mindset for him to be promulgating yet his naive followers lap it up.
My first reply pointed out that cryptography, the science of encrypting our data is far beyond our ability to crack it aka cryptoanalysis. I did concede that with the advent of new technology such as quantum computing this may well change.
His reply was hysterical like something you would expect from /r/oldpeoplefacebook in ALL CAPS no less with way too much CAPSLOCK.
Not to mention the exclamation mark spam!!!!!!!!!

Neither does he, Brick. Neither does he.
As it stands presently, there are some algorithms that are technically unfeasable to brute force (sequentially enumerating all possible key combinations).
For perspective, let's take the algorithm employed by the government, Advanced Encryption Standard (AES). I quote from the following from How secure is AES against brute force attacks?
Faster supercomputer (as per Wikipedia): 10.51 Pentaflops = 10.51 x 1015 Flops [Flops = Floating point operations per second]
No. of Flops required per combination check: 1000 (very optimistic but just assume for now)
No. of combination checks per second = (10.51 x 1015 ) / 1000 = 10.51 x 1012
No. of seconds in one Year = 365 x 24 x 60 x 60 = 31536000
No. of Years to crack AES with 128-bit Key = (3.4 x 1038 ) / [(10.51 x 1012 ) x 31536000]
= (0.323 x 1026 )/31536000
= 1.02 x 1018
= 1 billion billion years
This article was written in 2012 and current supercomputers have become much more capable.
Per this article from 2018, the fastest supercomputer at the time was capable of 200 petaflops dwarfing the one referenced in the 2012 article.
Let's do the math!
(((10^15)200) /1000) / 31536000*
Can I get a drumroll please? The results are in!
Based on 2018 supercomputing technology, it would take approximately 6341958.39675 years to crack an AES 128 bit key using a brute force attack. That's over 6 MILLION YEARS.
Ain't nobody got time for that!

Quite literally.. unless you're a vampire or otherwise immortal.
Bonus Challenge!
Your mission if you choose to accept it
Obtain more recent figure for floating point operations per second, cite the article, perform the same math, and state the results in a comment. If you do this, I will use my SFR (@steemflagrewards) credits to boost that comment with a full upvote from our bot. Also, I will curate one of your recent posts as well. First one wins!

We have established the basis for cryptographic technology exceeding cryptoanalytical. That, in and of itself, doesn't debunk what McAfee is trying to assert. Specifically, that all systems are compromised BEFORE the secure channel is established thus making them all insecure by default. I have an answer for that which will be stated later.
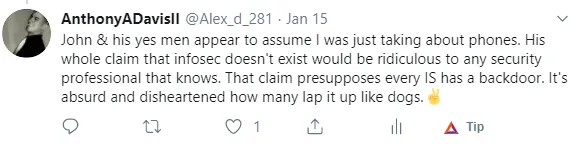
Yes, at this point I was beginning to get a little ticked.
After about the first 7 retweets, I had to mute the conversation otherwise I may have blown a blood vessel out of frustration from the utter mindlessness of it all.
I was done or so I thought..
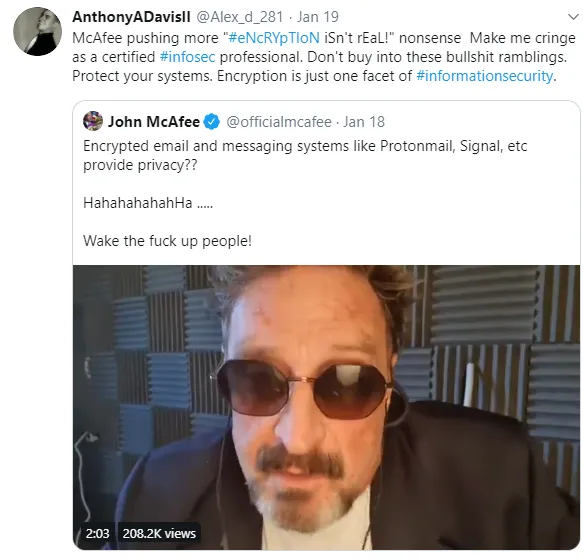
Here we go again
I was checking out a profile of another Steemian and noticed he was at it again.
Our fellow Steemian and IT professional @joshman even got his 0.02 SBD in!
I imagine McAfee is the type of guy that would be living in a Faraday cage
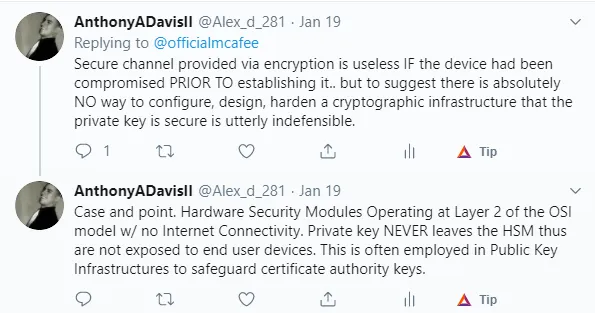
So, are you drinking the McAfee Koolaid. Do you honestly believe every information system (IS) is compromised from the git go thus making the task of encrypting your data a fool's errand? Well, I got something for you.

Enter the Hardware Security Module (HSM)
If you had been following me, you may have recalled my mentioning going to Florida to obtain another certification. It was a weeklong training and I had to pass a final exam. It wasn't cheap either.
$3000 that was thankfully reimbursed but the airfare was on my dime. Felt it a necessary expenditure considering the nature of my work. However, reimbursement was contingent on my passing which led to a few tense days afterward while the exams were graded.

But I managed to pull it off which I suspect was by the sweat of my chinny chin chin. 😅
Anyways, I tweeted the details of a theoretical implementation that would lay this silly notion to rest.
You're probably wondering.. What the hell is an HSM? I could go about explaining it myself but I'll let the following training slides do the talking.
Also, I may caveat that, unlike McAfee, I AM NOT A SHILL. I don't promote things because someone is paying me to do so.
Rather, I do it because I know and believe in the technology
Let's get into the slide deck, shall we?
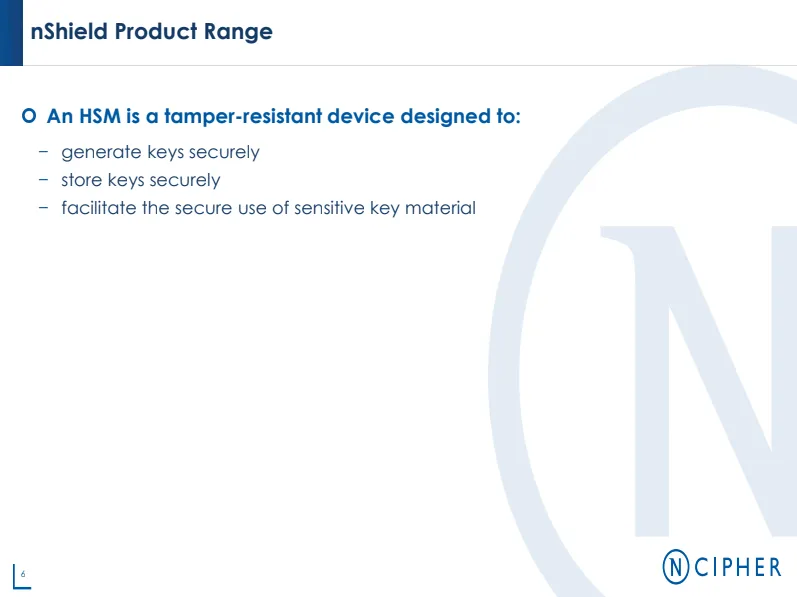
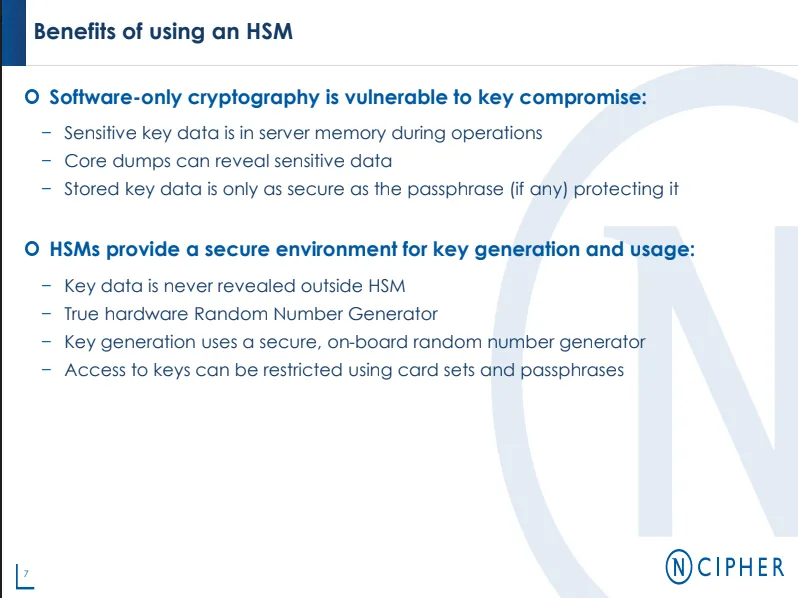
Seems like a pretty nifty appliance... because they are! I'm also very much interested in the applicability of this tech to cryptocurrency.
Think about it.
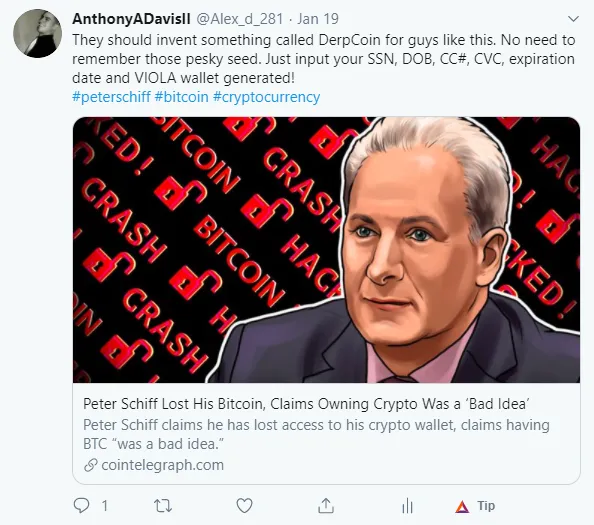
How many times have you heard about a user forgetting their private key and losing their funds?
Sure a few of yall had heard about economist Peter Schiff recent ordeal. Yes, I had to poke a little fun at it.
Perhaps, a DERPCOIN whitepaper will be forthcoming.
Let me know if you would like to see that to push it up in my work queue.
It is somewhat speculative on my part that HSMs can be used to secure crypto wallets but I am definately interested in pursuing that idea further. I just need to get my hands on a personal HSM and begin tinkering with their developer API.
If any potential benefactor is interested in assisting me monetarily in getting that project started, feel free to contact me on any of my social media accounts.
I will need the funds to purchase the device, card sets, and required licenses which are currently outside of my means as I work off a revolving credit card debt. I'll be there soon enough. If you would like to support me in spearheading this thing before someone beats us to it, we can work out a deal.
At this point, I think I've said enough. (Probably too much)
I believe the reader will now at least see things from a more informed perspective than McAfee is providing his followers. Our sensitive data is important, folks! We should not be lax in safeguarding it.

Not just for us individually but also our families. I wouldn't want any of my followers or readers to get burned due to his misinformation. If you consider yourself to be in the personality cult of McAfee, it is my sincere hope that you at the very least approach his claims with due diligence and a measure of skepticism. As I have had today...
Put it to the test!
I just gotta point out the irony of the famous Antivirus pioneer making misleading claims about information security. Just goes to show that we shouldn't blindly follow any Internet persona.


Would you like to delegate to the Steem Flag Rewards project and promote decentralized moderation?
It's much more fashionable than self-voting.
Here are some handy delegation links!
Also, here is my SteemAuto fanbase link if you would like to be one of my consistent supporters.
A special thanks to @futuremind for encouraging me to create content like this.
P.S. This was created using the eSteem Surfer Desktop App and really digging it. I highly recommend it if you are on a Desktop.