Hi, today I will tell you how to search for vulnerabilities using the nmap tool, nmap next to Nessus is probably the best known tool to search for vulnerabilities, today it will show how to use it.
Run kali linux and type nmap -sC ip victim, in my case display:
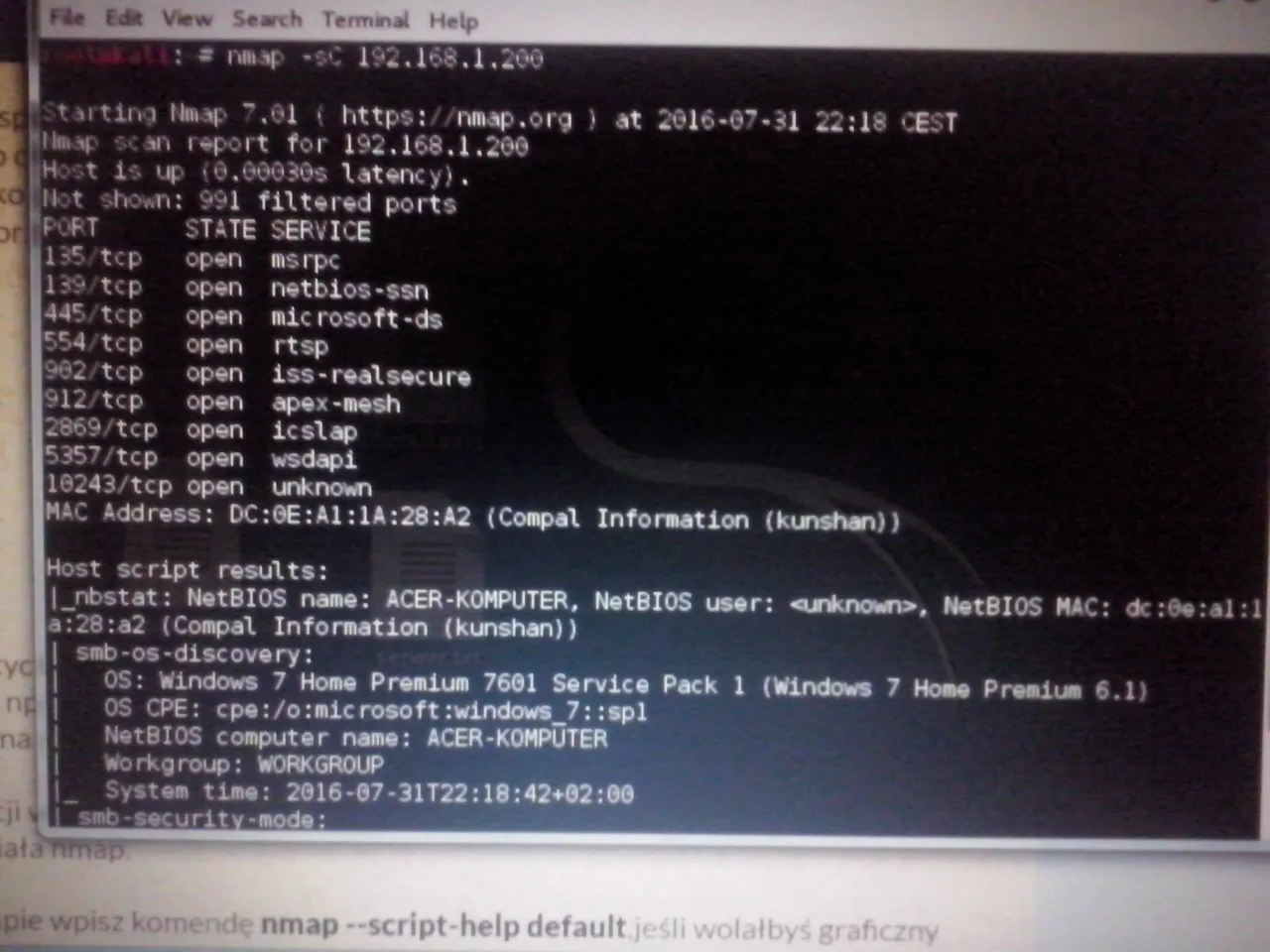
There are information about open ports, their numbers, used services, used system that informations might be very useful, for example if you want to upload an exploit to a specific operating system using metasploit, Mac address of the victim, etc.
If you want more information enter nmap -sV ip victim, there are many more commands, but I just wanted to show you how nmap works.
If you want to read about nmap, enter the command nmap -script-help default, if you would prefer a graphical interface nmap, go to the top tab “Applications” then in “Information Gathering” and at the bottom select the “zenmap” tab.
You enter the victim’s ip in the place “target”, select in the “Profile:” field, what type the scan is and choose the “scan” button, as you can see everything can be on-click, you musn’t amuse in the console.
As I mentioned, there is another very good tool for scanning “Nessus”, I will not describe it here on youtube, it is well described in this video:
Today I’ve described to you two very good tools to search for vulnerabilities, of course, there are many more tools to search for vulnerabilities, but for me these two are the most effective ones.
If you recognise it as useful, share it with others so that others can also use it and leave upvote and follow if you wait for next articles :)
For today, that’s all, bye !!!
