
In the evolving decentralized storage world, SPK Proof of Access (SPoA) is a new solution that enables the community to store backups of crucial, off-chain files on the IPFS network. The SPoA system also ensures that each storage node stores the files they claim to hold. SPK Proof of Access is part of the SPK network, a blockchain-based file storage system where nodes are rewarded in SPK cryptocurrency for storing files.
How Proof of Access Works
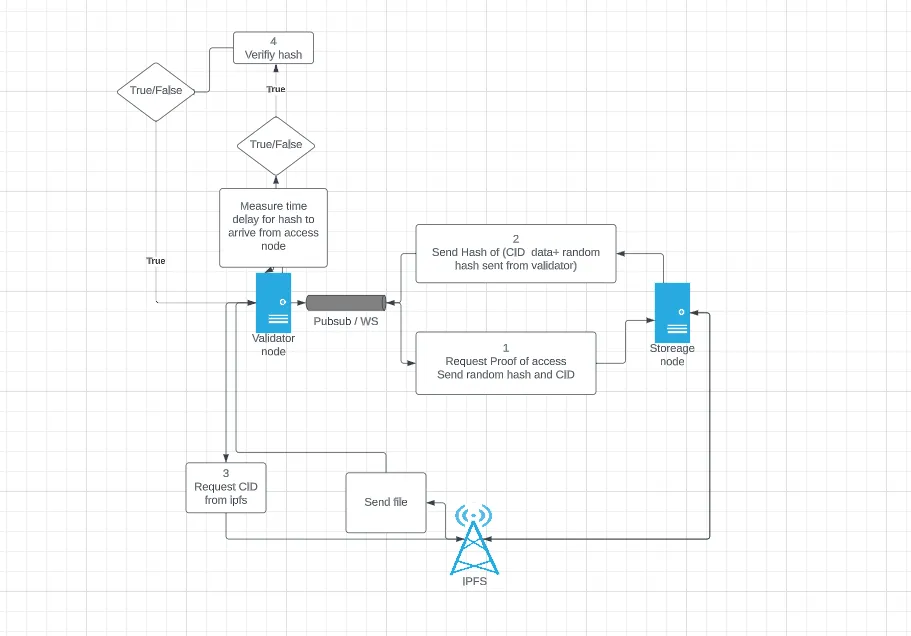
When a validation node needs to verify that a storage node is storing a file, it sends a request for proof of access to the storage node over either IPFS pubsub or WebSocket. The request includes a random hash and the CID of the file the storage node should prove they are storing.
To create the proof hash, the storage node uses the random hash to determine the first chunk of the file, it should use in this process. It then appends the random hash to the end of the IPFS chunk. The storage node then selects the next chunk of the file and appends the previous hash created to it, creating a new hash. This process is repeated several times, depending on the file size. The end result renders a proof hash.
After creating the proof hash, the storage node sends it back to the validation node. The validation node then checks if the storage node sent the proof within 500ms of being requested. If true, it runs the same algorithm, using the original salt hash sent to the storage node to create the proof. The validation is valid if the proof hash is the same as the proof hash sent from the storage node.
How SPoA Prevents Cheating
If a storage node stores the files they claim to store, it will produce a proof hash that matches the proof hash created by a validation node.
On the contrary, if a storage node cannot do this, they are not storing the file they claim. Therefore, SPoA prevents storage nodes from cheating the system and falsely claiming they are storing a file they are not.
Consequences of Failure to Provide Proof of Access
The storage node will not be rewarded if it fails to provide valid proof. Such a failure could damage the reputation of the storage node, with a possible loss in future earnings. Validators caught collaborating could face similar consequences, potentially losing community votes.
The Advantage of Using 20 Stake-Weighted Community Elected Validators
Traditional blockchain systems that use proof-of-stake (PoS) or proof-of-work (PoW) mechanisms only store blocks after every node in the network has validated the data; Proof of Access (SPoA) operates on a more efficient and democratic model.
In SPoA, the task of validating is delegated to 20 stake-weighted community members who are elected to serve as validators. The SPK team chose this model based on its numerous advantages.
The first advantage is a significantly reduced computational and resource burden placed on the network. Leading to quicker, more efficient validations and a more scalable system overall.
Secondly, the election of validators by stake-weighted community voting introduces a democratic element, ensuring the system operates fairly and transparently. Those entrusted to validate are chosen by the community for the community, reinforcing the decentralized nature of the SPK network.
An essential aspect of this system is that all of the top 20 validators have an equal say on validation, regardless of the size of their stakes, ensuring that no single validator can disproportionately influence the decision-making process, promoting fair and equal representation.
Another advantage is that validators are voted for based on reputation, performance, and the community's approval. The fact that the community can remove validators incentivizes honesty. It fosters a healthier and more accountable network where validators are motivated to act in the best interest of the SPK network.
In essence, Proof of Access leverages the strength of community involvement and efficient validation processes to offer a superior, democratic, and scalable system for decentralized file storage.
Credits
Nathan Senn (@nathansenn) developed SPK Proof of Access, and it is available on GitHub at https://github.com/spknetwork/proofofaccess.
The SPK Network funded the development of SPoA. If you believe in a more transparent and secure internet, show your support for this transformative technology by voting on the SPK network funding proposal found at @spknetwork/spk-network-funding-proposal-rhnv7e.
Special thanks go to @theycallmedan, @starkerz, @vaultec, and @disregardfiat for their contributions and support.
Conclusion
Proof of Access is a powerful mechanism to validate that a storage node stores files on its local IPFS node. This technology will play a vital role in the SPK network, where storage nodes will be rewarded with SPK cryptocurrency for their storage services. SPK Network's Proof of Access provides the solution by offering an effective way to verify the integrity of stored files. Verify the reliability of storage nodes without blind trust, true Web3 data storage on the Hive blockchain.
License
SPoA is free and unencumbered software released into the public domain under The Unlicense. For more information, please refer to http://unlicense.org/
Contact
For any inquiries or issues related to this integration, you can contact Nathan at nathan@d.buzz.
Discord: nathansenn
Follow on D.Buzz at https://d.buzz/@nathansenn.
About the SPK Network:
The SPK Network is a decentralized Web 3.0 protocol that rewards value creators and infrastructure providers appropriately and autonomously by distributing reward tokens so that every user, creator, and platform can earn rewards on a level playing field.
Check out the SPK Network Light Paper: @spknetwork/spk-network-light-paper
Visit our website: https://spk.network/
Telegram Group: https://t.me/spknetwork
Discord Server: https://discord.gg/JbhQ7dREsP