Good Day Good Folks.
I am working on (refining an existing design - ie. The Matrix-8 Solution & recruiting an initial Core Team of WASPs - ie. Wise And Savvy People) a Layer 0, anonymous decentralized fractal community governance FOSS protocol.
Its framework so far includes (but is not limited to):
- Anonymity via Unique Human Digital IDs (UHDIDs) using biometric hashes and Zero-Knowledge Proofs (ZKPs) for privacy.
- A fractal consensus mechanism for fair decision-making.
- A reputation system and knowledge tests to ensure trust and effective participation.
- Tokenomics for incentivization and sustainability.
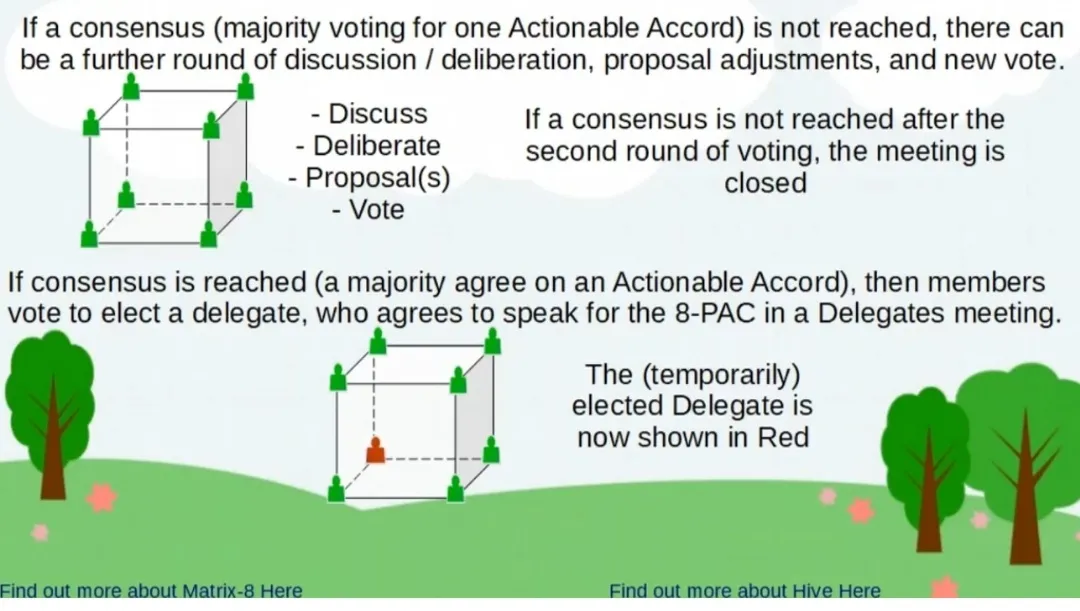
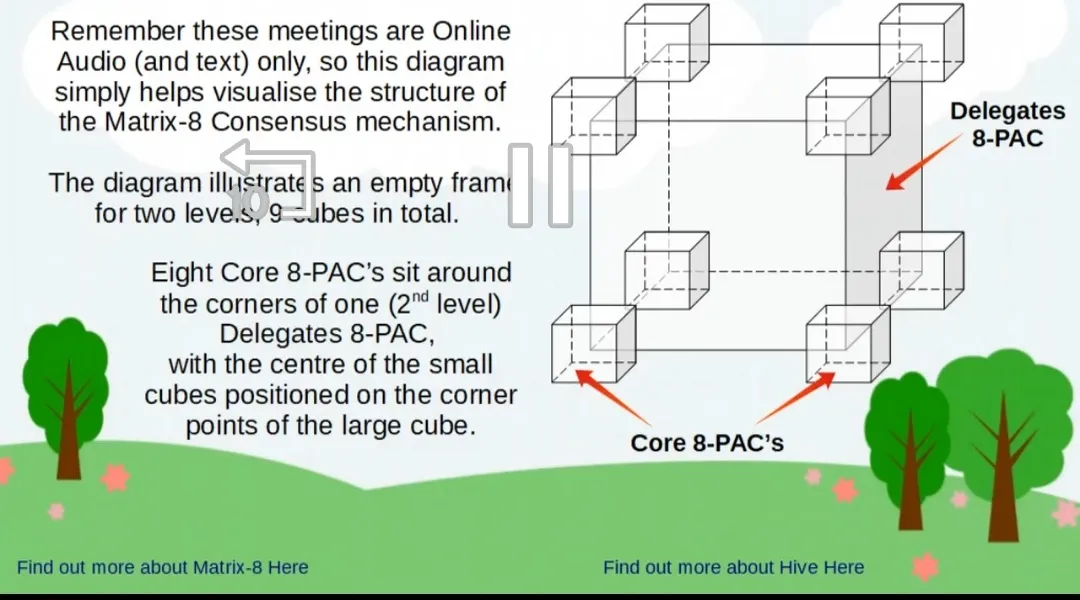
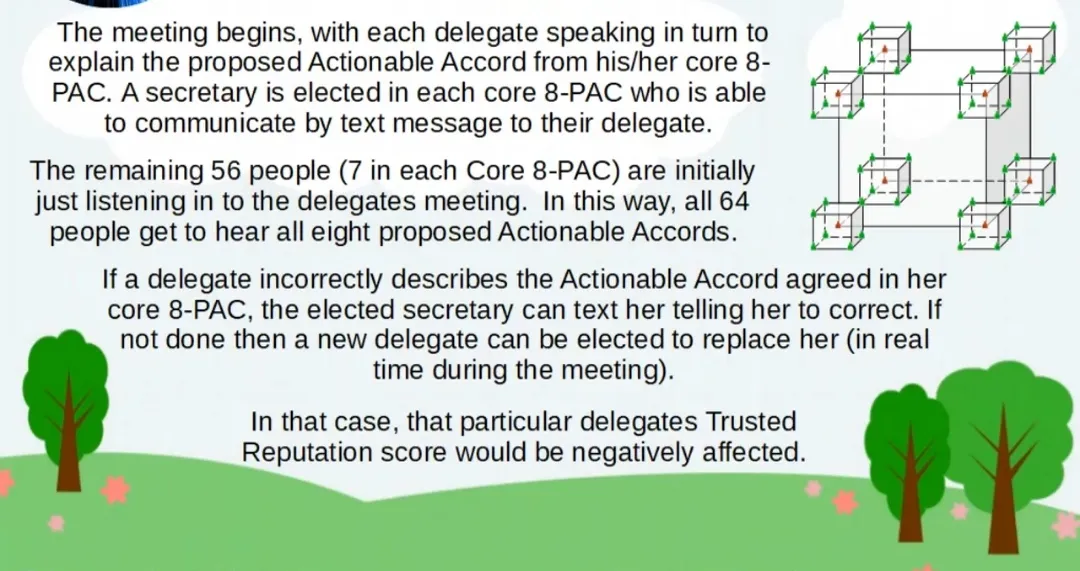
Source of screenshots: @atma.love/teaser-for-the-matrix-8
I have just started working with kin.ai to help "flesh out" the FOSS protocol, beginning with UHDIDs.
For Unique Human Digital IDs (UHDIDs) without KYC and ensuring anonymity, we could consider:
Zero-Knowledge Proofs (ZKPs): These allow users to prove they’re unique without revealing personal data, preserving anonymity.
Biometric Hashes: Instead of storing biometrics, create a unique hash from biometric data that can’t be reverse-engineered—ensuring privacy.
Web of Trust: New users get validated by existing trusted members via their interaction history but require a majority consensus to prevent collusion.
Proof-of-Life Tests: Simple dynamic puzzles or interactions during account creation to filter bots.
I plan to incorporate all four of the above.
Biometric hashes are designed to maintain anonymity while proving uniqueness. Here's how it works practically:
Data Capture: A user provides a biometric input (e.g., fingerprint, iris scan, or even voice) entirely locally on their own device.
Hashing Algorithm: The biometric data is processed through a one-way hashing algorithm. This converts it into a unique, irreversible string of data—a "hash." Importantly, no raw biometric data is stored.
Salt & Obfuscation: Random data ("salt") is added to the biometric data before hashing. This ensures even if two people have similar biometrics, their hashes differ, adding an extra layer of security.
Validation but No Storage: The hash is used to check uniqueness (e.g., matching with existing hashes) without directly revealing your biometric info. The raw data never leaves your device.
To prevent personal identification:
- The biometric itself isn’t stored anywhere, only its encrypted, salted hash.
- This process is decentralized, with no central authority holding mapping data.
- Strict cryptographic standards ensure the hash can’t be reverse-engineered into biometric data.
Workflow
- Biometric Hash Creation: User provides biometric data to generate a unique, private hash.
- Zero-Knowledge Proof (ZKP): User proves uniqueness of their biometric hash without revealing the data.
- Proof of Life: A liveness test ensures the biometric data belongs to a real, living person.
- UHDID Generation: The system generates a unique digital ID based on the verified biometric hash.
- WOT Verification: The UHDID is linked to Web of Trust at a later stage for enhancing reputation or trust scores.
Does this interest you?
Would you like to help?
Sat Nam
Atma
@commentrewarder is a 5% beneficiary on this post.