The new cybersecurity tool: tokenization.

An interesting concept in business is that things invented for one purpose are often used for an entirely different one. Sometimes the use case the technology wasn't invented for, becomes its biggest use case. An interesting example is tokenization, originally invented as a finance tool, but it can also be used in cyber security.
But before diving right into the use case I think some background information is useful.
The definition of Token, or token, is very contextual and varies from the cyber security aspect of Tokenization—which underlies payment systems like ApplePay and Android payment systems utilizing your phone—to Tokens having value in cryptocurrency blockchains. Each topic is fascinating, but let’s look at how Tokenization can help your company with cyber security.
A day hardly passes that we don’t hear about a online computer “hack” of some type or another. We cringe when we hear some big commercial entity had their customer database “hacked” and thousands or even millions of customers private information was stolen by criminals for sale to other criminals for illegal activities including identity theft.
Several companies have been created who produce computer software to detect and inactivate computer software programs designed to facilitate or carry out this theft from the computer databases of commercial entities. cyber-security Tokenization provides a different method of protecting your company computer databases from being attacked and your customers sensitive data bring lost. It is based on the “Willie Sutton” rule.
Willie Sutton was a famous bank robber in America from 1901-1980. He carried out hundreds of bank robberies and when asked why he robbed banks he replied “Because that’s where the money is.”
The modern day cyber security application of the “Willie Sutton” rule is that computer “hackers” break into commercial databases because that’s where the valuable customer data like names, addresses, credit card numbers and credit card expiration dates are stored.
Before cyber-security tokenization was created efforts to protect customers data centered on building stronger locks on the doors called “Firewalls” to keep the data thieves out. Secondary methods used “guard dogs” called virus-detection software to detect programs which hit past your “firewalls”. But now Tokenization is a new solution: the data isn’t stored on company computers, so when thieves break in they get data that’s worth nothing! So basically CyberTokenization has moved the money.
Cyber-security Tokenization creates account numbers made of complex alphanumeric sequences to represent sensitive customer data. These account numbers are long chains of numbers and letters which are completely unrelated and not derived from the underlying customer data. It’s a string of letters and numbers. By themselves they aren’t worth anything! The commercial entity still collects customer information for order purchases, payments and delivery, but the data is immediately given to the cyber-security company and never stored on commercial-company computers. This sensitive and valuable customer data is then “Tokenized” by assigning it this alphanumeric account number which is stored on the commercial-company computers. The cyber-security company then stores the actual customer data in encrypted data packets, basically locked data files with a complex unlocking codes in a vault in a different physical location.
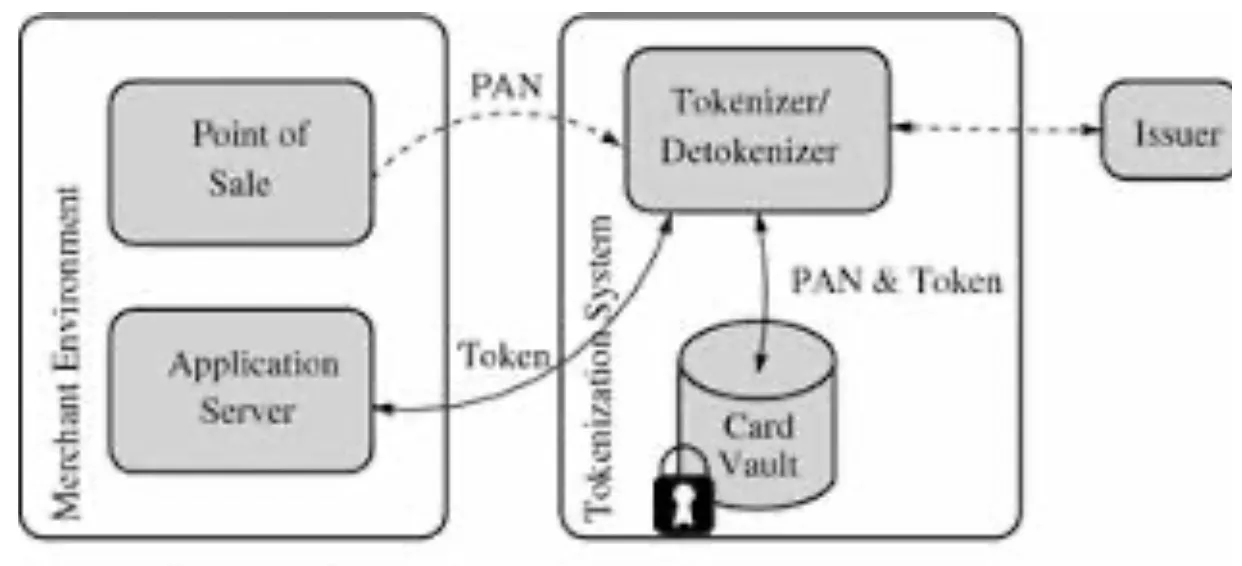
Cyber-security companies now use its online computers to store information it wants website visitors to see! Like its products and prices! While sensitive customer information is not stored on its computers servers. The majority of its employees never see sensitive customer information. Their focus is on the companies goods and services. So now the company can focus on its core mission creating great products or services its customers want to buy.
You’re probably thinking, Wow!
This is wonderful!
But how much does it cost?
And is anybody actually doing it?
Well the answer is it’s cheap and yes.
I don’t know where the idea originated, it’s origins are open source, but this particular “Cyber Security Version” of Tokenization is being used by many companies world-wide and has been made famous by Apple Pay and The Android Store. These phone payment systems use a computerized system which allows you to make purchases from various product and service vendors and you never give them your credit card number, card expiration date or other sensitive information. Tokens are created, sent to Google servers, banks, the vendors and money hoes to the vendors account fir your purchase in seconds. The adaptation of this technology protects customers from the theft of their sensitive information, protects the product and service vendors from computer thieves hacking and shutting down their computer systems and protects them from lawsuits and loss of business which accompanied these computer hacks and customer information thefts.
It’s a win-win situation, for everyone except the thieves and we can thank Willie Sutton. He indirectly explained that the best way to prevent bank robberies was not stronger doors and more guards. But to stop keeping the money there.
The End..for now.

About @shortsegments
Shortsegments is a writer focused on cryptocurrency, the blockchain, non-fungible digital tokens or NFTs, and decentralized finance. He has been a community member for more then three years.
He is also a builder, with two current projects:
The first is the No Loss lottery, a prize linked savings account here on Hive, which awards more the 100 Leo in prizes weekly, and which recent surpassed 1000 tickets sold. @nolosslottery
His second project is Easy DeFi, which creates a community investment pool allowing community members not yet confident enough to invest on their own, a chance to easily invest in yield-farming and staking on Cubfinance. @easydefi
Yield Farming
Cubfinance is the Hive communities home grown Yield Farm and is audited by CertiK, a third party which certifies DeFi projects on Ethereum, Binance and polygon ecosystems.
Read more of shortsegments articles here: @shortsegments
Leofinance, where you can blog or share financial topic content to earn cryptocurrency, as part of a passionate social media community.

GIF created by @mariosfame
Learn more about Leofinance with my Seven Minute Quick overview and QuickStart Earning Guide. Then you can Join for FREE! Signup takes 20 Seconds!
Click Here
