From Wikileaks VAULT7 -
HIVE is used across multiple malware implants and CIA operations. The public HTTPS interface utilizes unsuspicious-looking cover domains to hide its presence.
Anti-Virus companies and forensic experts have noticed that some possible state-actor malware used such kind of back-end infrastructure by analyzing the communication behaviour of these specific implants, but were unable to attribute the back-end (and therefore the implant itself) to operations run by the CIA. In a recent blog post by Symantec, that was able to attribute the "Longhorn" activities to the CIA based on the Vault 7, such back-end infrastructure is described:
For C&C servers, Longhorn typically configures a specific domain and IP address combination per target. The domains appear to be registered by the attackers; however they use privacy services to hide their real identity. The IP addresses are typically owned by legitimate companies offering virtual private server (VPS) or webhosting services. The malware communicates with C&C servers over HTTPS using a custom underlying cryptographic protocol to protect communications from identification.
The documents from this publication might further enable anti-malware researchers and forensic experts to analyse this kind of communication between malware implants and back-end servers used in previous illegal activities.
@ackza/wikileaks-org-vault8-hive-cia-project-hive-2017
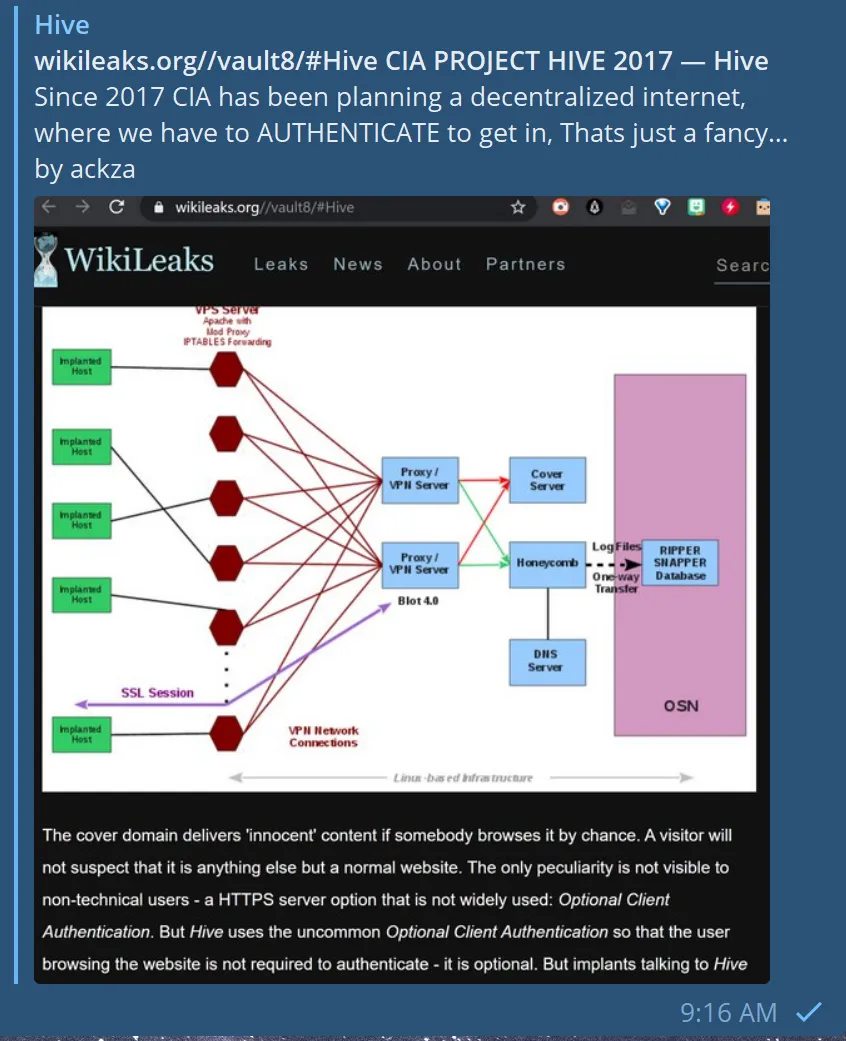
https://wikileaks.org/vault7/#Hive
https://wikileaks.org/vault7/#Protego
Protego seems to be about @challengedac GPS
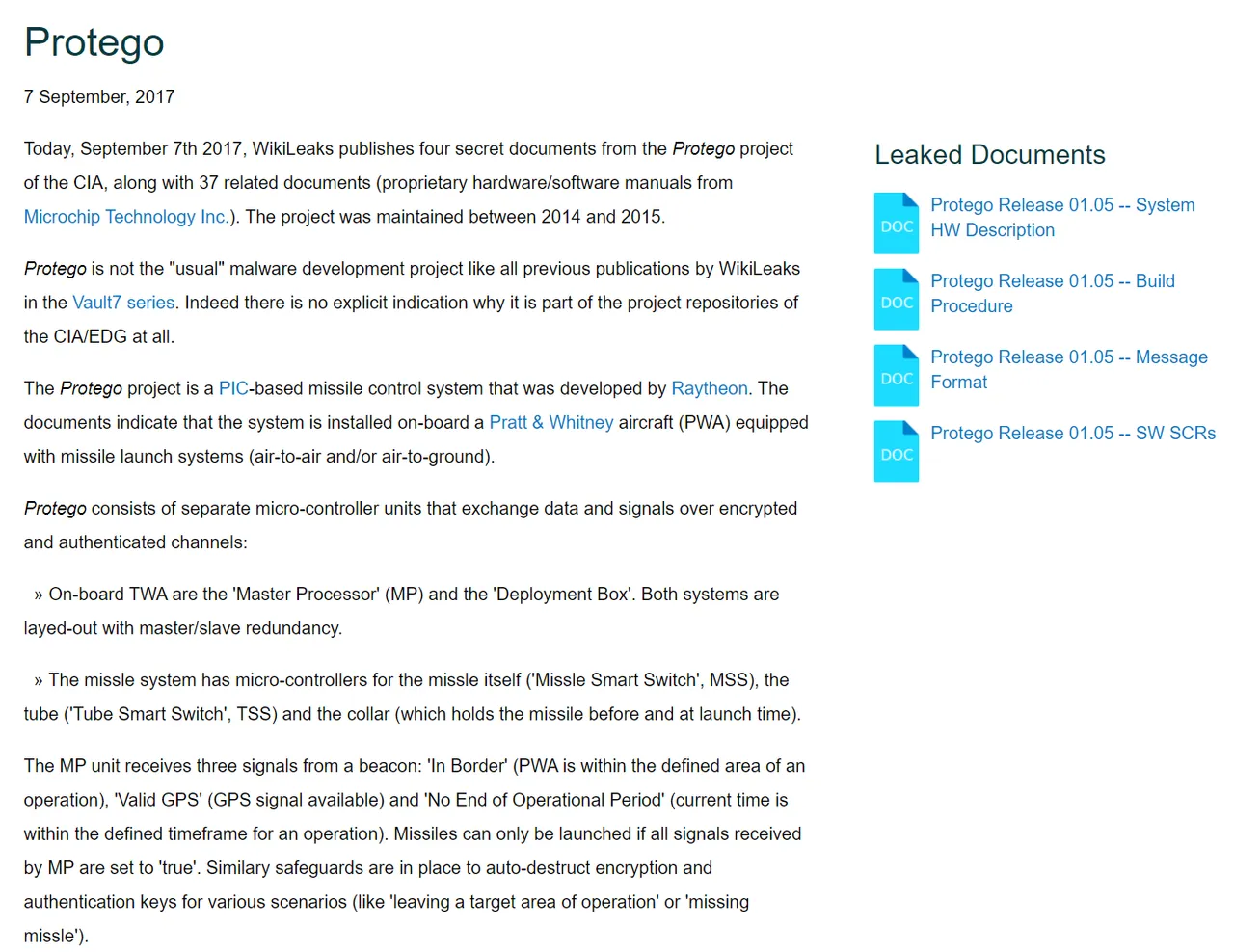
Protego
7 September, 2017
Today, September 7th 2017, WikiLeaks publishes four secret documents from the Protego project of the CIA, along with 37 related documents (proprietary hardware/software manuals from Microchip Technology Inc.). The project was maintained between 2014 and 2015.
Protego is not the "usual" malware development project like all previous publications by WikiLeaks in the Vault7 series. Indeed there is no explicit indication why it is part of the project repositories of the CIA/EDG at all.
The Protego project is a PIC-based missile control system that was developed by Raytheon. The documents indicate that the system is installed on-board a Pratt & Whitney aircraft (PWA) equipped with missile launch systems (air-to-air and/or air-to-ground).
Protego consists of separate micro-controller units that exchange data and signals over encrypted and authenticated channels:
» On-board TWA are the 'Master Processor' (MP) and the 'Deployment Box'. Both systems are layed-out with master/slave redundancy.
» The missle system has micro-controllers for the missle itself ('Missle Smart Switch', MSS), the tube ('Tube Smart Switch', TSS) and the collar (which holds the missile before and at launch time).
The MP unit receives three signals from a beacon: 'In Border' (PWA is within the defined area of an operation), 'Valid GPS' (GPS signal available) and 'No End of Operational Period' (current time is within the defined timeframe for an operation). Missiles can only be launched if all signals received by MP are set to 'true'. Similary safeguards are in place to auto-destruct encryption and authentication keys for various scenarios (like 'leaving a target area of operation' or 'missing missle').
End of Service
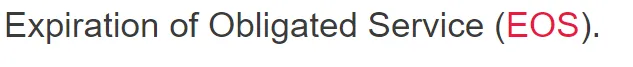
Expiration of Obligated Service (EOS).
https://military.wikia.org/wiki/End_Of_Active_Service
https://masseffectandromeda.gamepedia.com/Eos:_The_First_Outpost
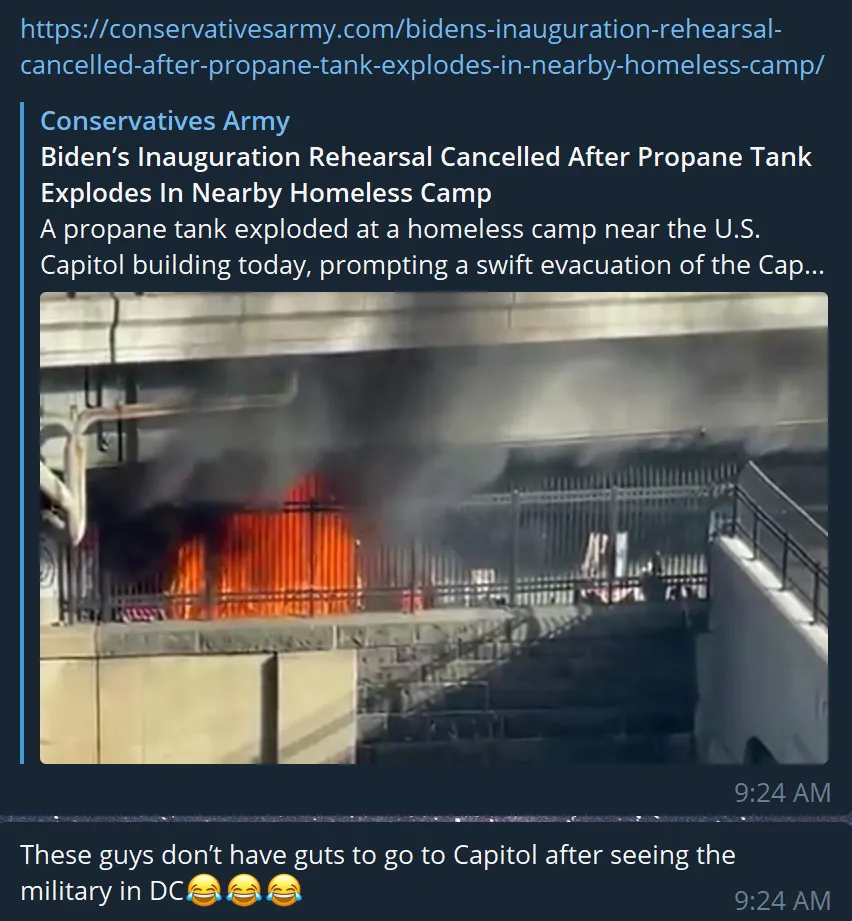
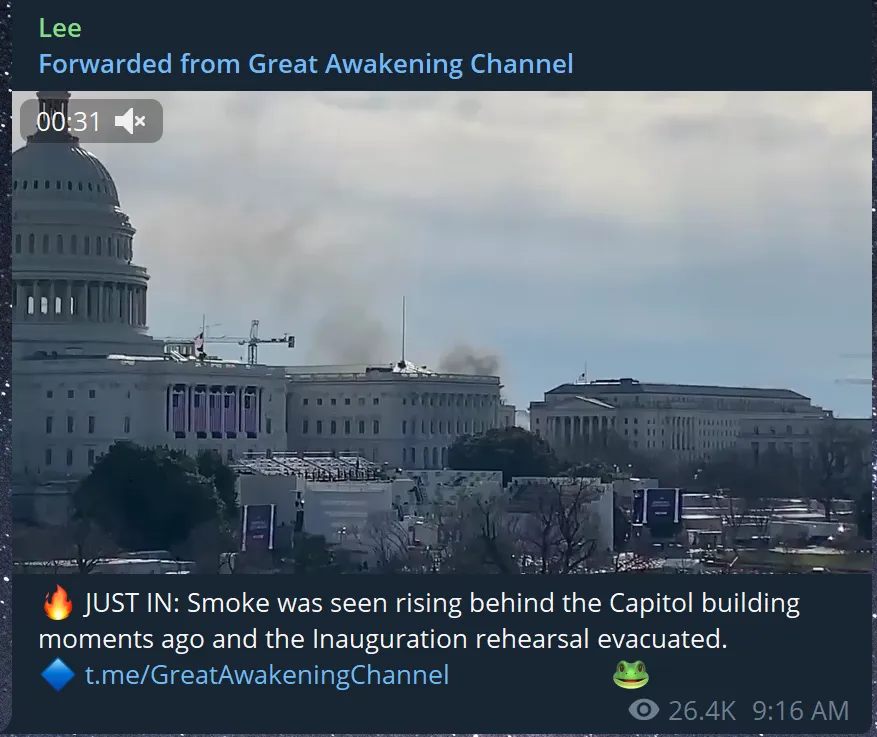
Whats Going On?
What will the Future Hold?
Consult the ORION SPHERE
The Women are in control



