Paying more attention to the code of the main known VQGAN+CLIP colab notebooks,, i noticed that the script is encoding in each picture created, the following encrypted information.
def add_stegano_data(filename):
data = {
"title": " | ".join(args.prompts) if args.prompts else None,
"notebook": "VQGAN+CLIP",
"i": i,
"model": model_name,
"seed": str(seed),
}
lsb.hide(filename, json.dumps(data)).save(filename)
This means that some text information are encoded, hidden, into the bytes of the picture file using a method called Steganography
Nowadays, some online tools enable to decode such text from a picture on the fly. As a demonstration i took a picture i created with VQGAN+CLIP some months ago when i was busy with my imaginary city guide.my imaginary city guide. Note that this picture has not been used in this guide.
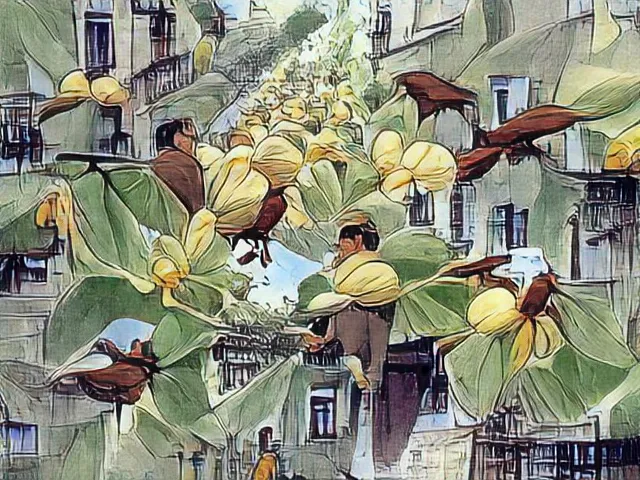
So i submitted the following picture to the decoding process.
And the result was the following :
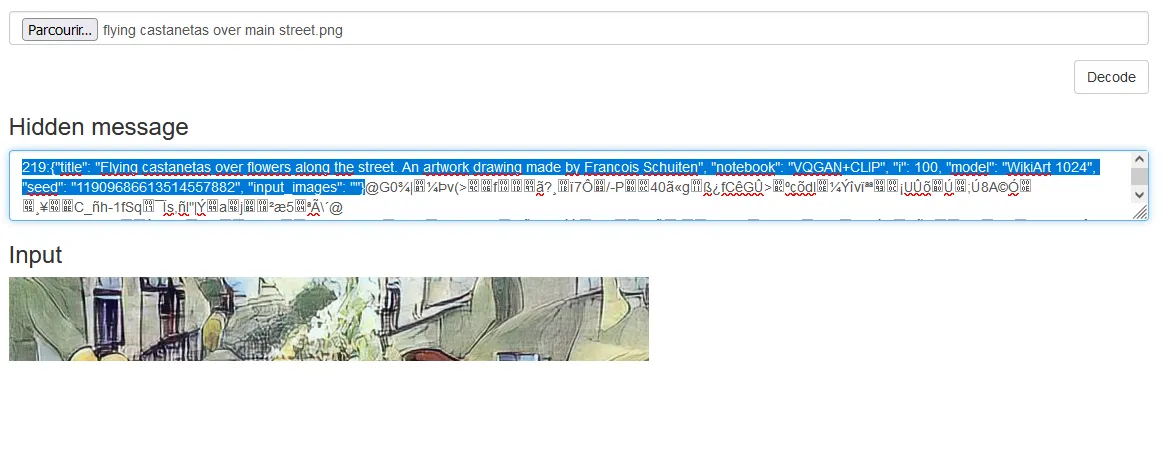
219:{"title": "Flying castanetas over flowers along the street. An artwork drawing made by Francois Schuiten", "notebook": "VQGAN+CLIP", "i": 100, "model": "WikiArt 1024", "seed": "11909686613514557882", "input_images": ""
At least, this can be useful to find back prompt you did not remember.
If you want to get rid of this when you use such colab notebook, just comment the following lines of the code like hereunder where i added the sign "#" :
def save_output(i, img, suffix=None):
filename = \
f"{working_dir}/steps/{i:04}{'_' + suffix if suffix else ''}.png"
imageio.imwrite(filename, np.array(img))
#add_stegano_data(filename)
#add_xmp_data(filename)
Now, i am also thinking that we can embed unique code or text message in our artwork as a kind of easter egg. But i still have to think about this...
I suspect some other notebooks to contain this stegnographic module as the section of code involved is present in a lot of derivation from the initial notebook.
My two cents.