This is the 2nd post of a series for teaching cyber-security in a coding-club. Read [part 1]

Where is he typing? and what do those commands mean?
1.1.2 The layers in a computer
Most of the time you interact with software like this:
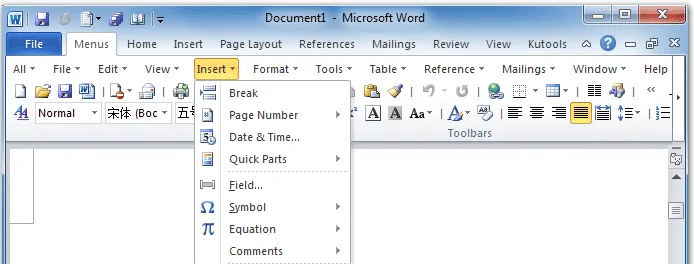
But do you know what's behind it? Every time you click or write, something happens behind the screen. for example. Let's say you click on the little info icon.
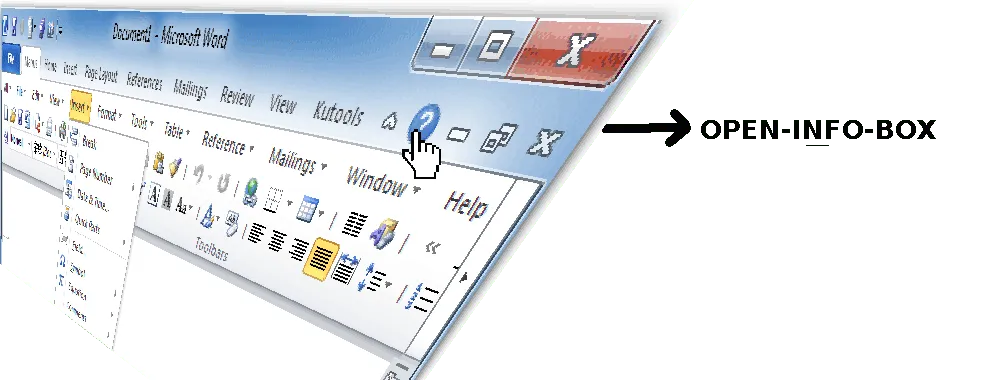
Behind that window, an order to OPEN-INFO-BOX is sent as a text command. But where does it go? A program (just like the ones you may have written in scratch, javascript or python) will read that order and decide what to do.
Once a decision is made, the screen needs to do something to respond. A new order is sent behind the scenes. The program now needs to talk to the machine. The actual chip in the machine.

Unfortunately, the machine only talks this language:
0110100001100101011011000110110001101111001000
0001101000011011110111011100100000011100100010000001110101
which means, hello how r u, in computer speak!
Between your click and the order in the chip there are many layers. The deeper you are in the machine, the more powerful things you can do.
Before the last layer is the nucleus (also called the Kernel, which means core in German). In this course you won't get access to the kernel, but you will get access to the layer above. It's called the Shell. You can imagine it as the shell surrounding the core of the computer.
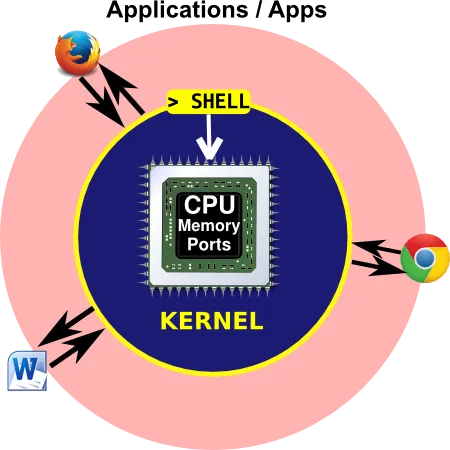
As a normal computer user you are only allowed to play with the applications (like Excel, Word or the browsers). However, for this course you will have access to The Shell.
The different layers on the computer are actually more complicated. There is also the OS (or the operating system which helps applications talk to the shell and the kernel and does some of the translation from the programs to the chip language of ones and zeroes -- 110101010!).
Here is a more detailed image of the layers:
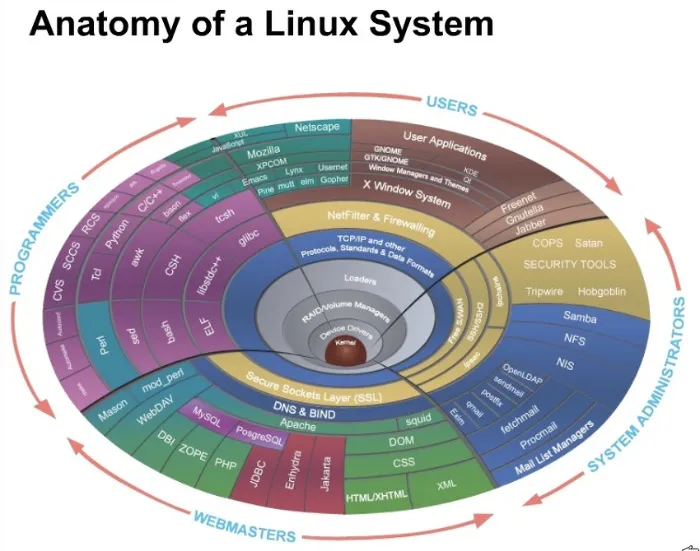
So let's open our own shell and learn what we can do with it. Continue reading [Part 3]