This is the 3rd post of a series for teaching cyber-security in a coding-club. Read [part 2]
Introduction
The shell is sometimes called terminal, command line interface or CLI. It's the place where you can send commands to the Kernel. Or the place where you can send commands behind the curtain.
This technology works with text commands typed line by line. You should have access to a shell which looks something like this:
source: linuxcommand.org
Ok, so let's get our current username:
- Click on the CLI
- Type:
whoami - Press the return key
Easy right? You've learned your first command:
 Command:
Command: whoami
Description: The whoami utility displays your current user ID as a name.
The little brain icon will indicate a definition which you need to learn.
 It's common to make typos
It's common to make typos
When typing commands in the CLI, it's common to make typos. Don't be afraid of some weird output in case you've typed something wrong, even the best developers make mistakes.
After typing the whoami command, you will have got:
user@machine:~/home$
user
The first line, where you typed the command, is called the command prompt. In the second line, we've got an output after executing that command by pressing the return key.
Basically, this is how the CLI works:
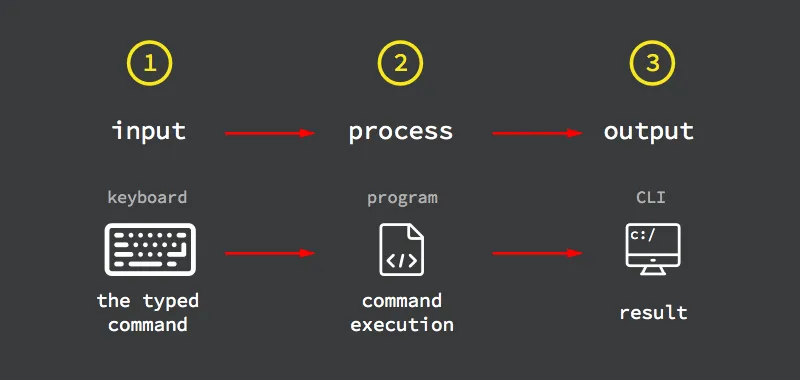 Source: codio.com
Source: codio.com
One important question to ask is how does the CLI recognize the whoami command?
How does the CLI recognize commands
Pay attention to the 2nd step of the program execution flow:
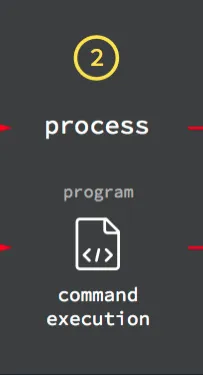
After hitting the return key, the CLI takes the whoami command and looks for a program with the same name somewhere in the computer:
command = program name
To better understand this, try to type any word into the command prompt and hit the return key, we'll use anyword as an example:
user@machine:~/home$ anyword
-bash: anyword: command not found
Did you get similar output?
The command line programs
The CLI recognizes several program names depending on the computer and the operating system that lives in the computer. A typicall shell or terminal window has an installed software called: bash.
 Bash
Bash
Bash is the name of the software that makes the interaction between the user and the terminal window possible. Bash has a vast catalog of program names, each of them performs different actions.
Ready to learn another bash command?
We already know how to get the current user with the whoami command, but what about getting the current working directory?
In other words, where we are right now inside the computer files and folders structure?
 Where we are right now inside the computer?
Where we are right now inside the computer?
Similar to the Mac's Finder or the Windows Document Explorer, the command line interface provides an alternative for navigating, displaying, editing, copying and moving files and folders across your computer's storage.
We will learn about it in [Part 4]