This is the 4th post of a series for teaching cyber-security in a coding-club. Read [part 3]
Where we are currently?
Remember that we said our server in Holland won't have a mouse, a keyboard or a screen. We will have to communicate with it through a command line interface (CLI) or a shell. As the shell does not provide a graphical user interface or GUI for clicking on files and folders, how do we know our current location inside the computer? How will we find or read a file?
 Folders = Directories
Folders = Directories
One important term that you need to know is that in cyber-security folders are called directories. So if you hear that hackers got into the root directory ... it's trouble! They got inside the main folder! Ok, so let's find out which directory we are in:
- Click on the terminal window
- Type in the
pwdcommand - Press the return key
 Command:
Command: pwd
Definition: The pwd command does not mean password, it means:
print working directory.
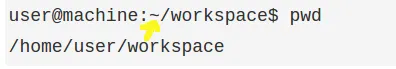
Understanding the pwd command output:
user@machine:~/workspace$ pwd
/home/user/workspace
Can you spot the similarities between the first line and the second line?
What exactly does the pwd command output?
The similarities between the first line and the second line of the previous example are that both are displaying the path to the working directory, in this case the workspace directory:
The workspace/ directory, is the folder called workspace
The workspace folder is specific to Codio. If you were to use the CLI on another machine, it could be some other location you choose to store your project files.
The home directory
What about the ~ symbol?
We learned that the pwd command prints the current working directory, in our case, the ~/workspace. But what about the ~/ that comes before the workspace directory?
The ~ symbol, better known as the tilde symbol represents the home directory, in other words the /home/user/ directory.
Imagine a scenario where the same computer is being used by 3 different users: John, Anita and Tom. The computer is automatically configured to have 3 different directories, each of them with the corresponding user name inside the home directory:
/home/john/workspace ~/workspace
/home/rita/workspace ~/workspace
/home/tom/workspace ~/workspace
John, Rita and Tom will have their own workspace directory without them getting mixed up with each others' files.
Listing directory contents
Let's list the ~/workspace directory contents
So we now know that we are currently in the /home/user/workspace. The pwd command tells us that.
How do we list what's inside it?
- Click on the terminal window
- Type
lsinto the prompt - Press the return key
 Command:
Command: ls
Definition: The ls or list directory contents command returns a horizontal list of the current directory and its contents.
Did the ls match the file list in your folder?
Considering that we are currently at the ~/workspace (remember this is equivalent to /home/user/workspace), then the ls command should have listed what's inside it.
Ok, so once you enter the secret server you will be able to list the files inside it. Continue reading [Part 5]