This is the 7th post of a series for teaching cyber-security in a coding-club. Read [part 6].
Hacking and protecting the secret server
Our mission is to get inside this server and fix the security:

In the previous unit, we learnt to interact with the shell to send commands to the core of the computer. We learnt to navigate the folders (called directories) and to find out what was inside them. The server we want to secure has no keyboard or screen, so we will need commands to talk to its shell.
You should have learnt the following commands:
whoamipwdto print working directorylsand the optionsls -a,ls -l
(Go ahead and try 3 options at once in the terminal:ls -alh: which means: list --all --list --human-readable)cdto change directorytouch somefile.txtto create some file.cat somefile.txtto see the content of the file
and finally some navigation tricks like cd .. to move up a directory level or cd ~ to move back to the home folder.
Let's learn some more interesting commands.
Installing software packages
Install anything
We are going to need more software in this machine to complete the mission.
Linux machines have a very special way to do this. As a Windows or Mac user you usually:
go on the internet => find an installer => download it => click on it => confirm => configure and install.
Most Linux machines have a powerful system called a package manager. Our software manager is called apt and most software can be found directly in the shell!
For example, let's say we want an antivirus. In your shell type:
apt-cache search antivirus
This should print a list of various antivirus packages. You can then install something you need with the command:
apt install SOME-SOFTWARE
Let's try it out. In the shell (also called terminal) type:
apt install sl
Did you get this error?
E: Could not open lock file /var/lib/dpkg/lock - open (13: Permission denied)
E: Unable to lock the administration directory (/var/lib/dpkg/), are you root?
To install software you need to be a Super User (like an administrator with special rights). Fortunately you can become one very easily. You just need to start your commands with the word sudo which means (Super User Do). So now try:
sudo apt install sl
Did it work?
Great Powers = Great Responsibility
Remember, now that you can use sudo you have full control over this machine on the internet. Don't break it! You will learn commands to install (but also delete) everything on this computer. So ask if you are in doubt!
Some playful commands
Testing our installation
You should have just installed the software called sl. This software is actually a small joke. It's very common to make typos. Woami instead of whoami, or sl instead of ls. So go to the shell and try this:
ls # (should print the list of files)
sl # (should print something surprising)
Try sl -F for the flying option! What did you see?
Ok, so you installed sl by using sudo apt install sl and it works. What other interesting tools can we install?
Want to impress your friends? How about a screen full of scary programs!
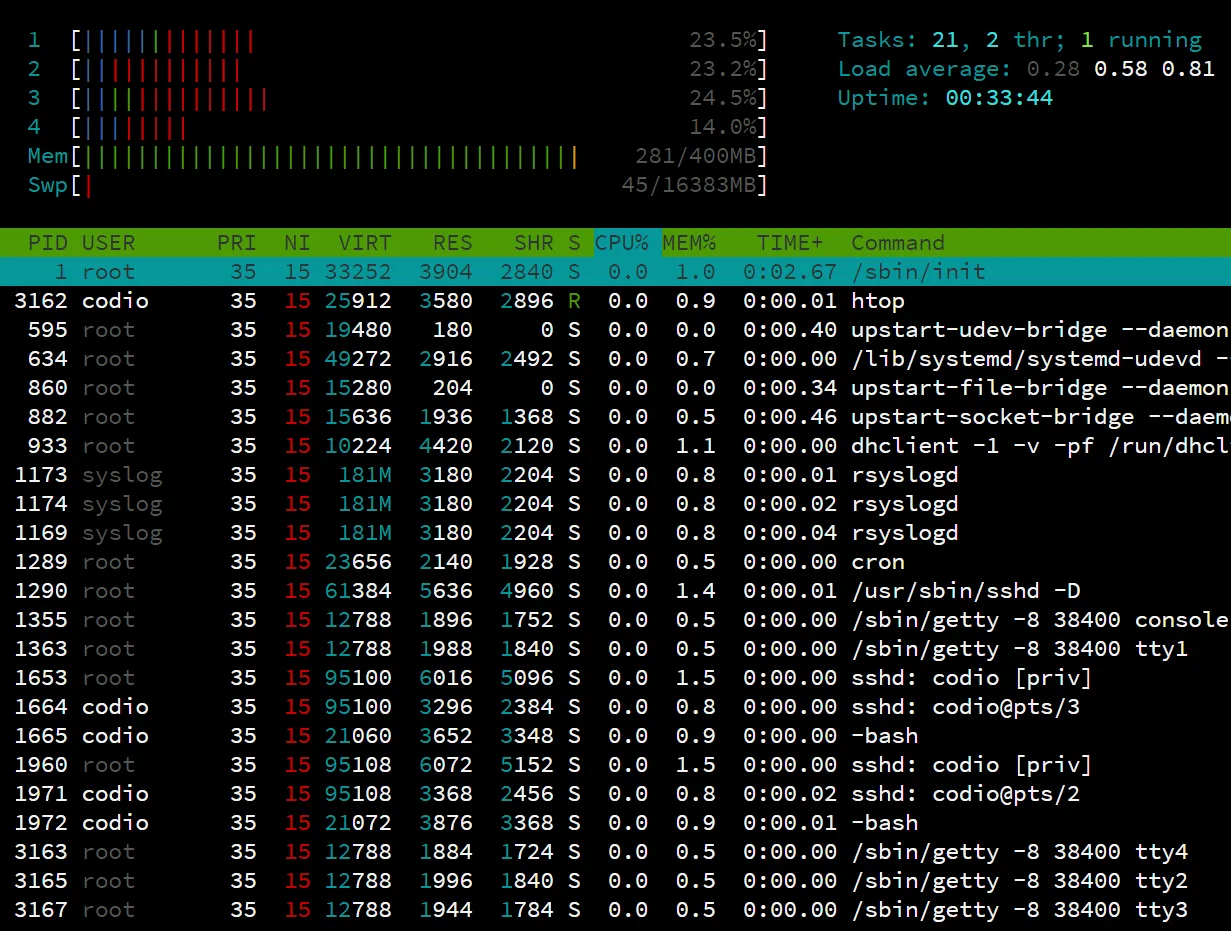
Source: https://hisham.hm/htop/
Before we do that, let's give you 2 helpful tips:
 Command
Command clear:
Definition:
The clear command clears the shell (or command line interface) screen. It can also be called with CTRL-L
Go ahead and try it out.
- To exit a program on the shell:
hit the letter
qto quit
Or you can hit CTRL-C
Ok, so let's install a program called htop. Try to do it yourself, and if you can't, just follow the instructions above for installing sl.
To continue learning for your mission, jump to [part 8].