
Have you heard about Coinhive? Coinhive is a malicious browser-based cryptocurrency mining snippet, that website owners can include in the website. As an unsuspecting visitor comes to the website in question, Coinhive miner will secretly use that visitors processing power to mine Monero, the privacy coin.
In October2017, Check Point Software, a cyber-security firm, announced that Coinhive is already the 6th most common malware in the world. What enourmous number of users are already affected by it, we can only guess. Maya Horowitz, a manager at the cyber-sec firm, said that "crypto mining is new, silent, yet a significant threat".

Via coindesk.com
Already at the end of last year we got reports, that Coinhive has taken this new threat one step further. Apparently websites running the Coinhive script, can now, after the user closes the tab, open browsers as a background process and keep mining, using the users computing power. Earlier this could only be done, when the user under attack remained on the website.
Why is this significant? Because most popup-blockers are helpless against this type of trickery by the malicious script. Luckily many antivirus apps are able to detect and block Coinhive from running and there is also a nice range of browser extensions made specifically to block Coinhive.
One of the most famous is No Coin, available at the Chrome Store for free. Follow this link to get it.
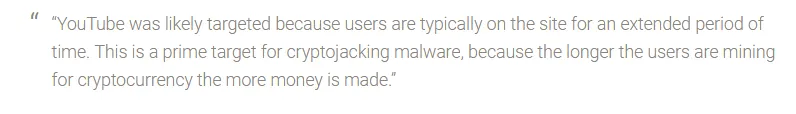
But now we get to the most recent news. According to a report by Trend Micro, they observed the detections of Coinhive miners tripling. And the reason for this was, as they called, "a malvertising campaign". Coinhive miner has been injected into Google's Doubleclick ads, which might trick users with false warning about malware. One of the most affected websites was Youtube, where users started complaining, that staying on the site, drains their CPU power. Accoring to an independent reseacher, Tony Mursch, Youtube was probably targeted as users tend to stay on that site for extended periods of time.
According to Google, this issue was fixed almost immediately, but Trend Micro claims they have evidence, that indicates that the malicious scripts were running for at least week after Google reported this issue fixed. According to TM, the jump in the number of miners on January 24th, was a whopping 285% and according to some experts, they expect this number to grow even more.
What can you do to protect yourself?
Installing the No Coin browser extension and blocking javascript-based apps in browser settings is a good start.
Be safe out there.
Sources:
https://bitsonline.com/computer-mining-cryptocurrency/
https://www.coindesk.com/coinhive-cryptocurrency-miner-is-6th-most-common-malware-says-report/
ttps://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/coinhive-miner-the-6th-most-common-malware
bitsonline.com - Illegal Cryptocurrency Mining Scripts Target YouTube Viewers
Check out Chainbb, an alternative frontend for STEEM network. If you like forum style, that's the platform for you.
Title image from pixabay


Are you looking for Minnowbooster, Buildteam or Steemvoter support? Or are you looking to grow on Steemit or just chat? Check out Minnowbooster Discord Chat via the link below.

BuildTeam