I decided to give the Dashlane password manager a shot. I've been happy with my current password manager, Passpack for several years, but a friend recommended Dashlane, so I thought I'd give them a quick try, see if it was worth switching.
So I set about creating my account on Dashlane, and step one was to enter my email and password. This is a password manager, so I won't use the usual crappy passwords that I might use to quickly post a comment on XYZ blog; I'll use one that won't cave easily.
When I want such a password, I try to construct random nonsense sentences, like Young thieves are edified by discovering the locks in the iron web. I came up with that one by looking at the stuff scattered across my desk and assembling random words and phrases into a sentence. I would bet money that, properly stored, that password will never be cracked in a password database dump. If the NSA decided to target that password in particular and dedicate a datacenter to it, OK, it might go down, but that's not what I'm trying to protect against. And I predict that password would put up a mighty fight before succumbing anyways.
The point of such a password is length and unpredictability. I would use such a password when I don't expect to type it very often, but I care a great deal about what it's protecting, and I want to make sure I won't forget it. This is important with password managers, because the good ones won't give you any recourse if you forget your password. They can't. If they can, that means that your password doesn't prevent them from accessing your data, and in the case of a password manager, that's unacceptable.
So I tried to create my account using a highly secure and easily memorable sentence-style password. Dashlane rejected my password, because it didn't have a number in it.

Let me remind you, Dashlane is a password manager. Do you expect a password manager to understand password security? Maybe? Just a little bit? So congratulations, Dashlane, you get another one:

Now, there's a lot of conflicting information out there on what makes for a good password. As with almost everything, most of the advice out there is really terrible. To most readers, it isn't immediately obvious why Dashlane deserves three facepalms here, but I hold a password manager company like Dashlane to a higher standard: I expect them to already be intimately familiar with the discussion.
For the rest of us, who haven't started a company whose purpose is helping people pick strong passwords, here's an XKCD comic that examines the issue of password quality:

I realize that XKCD is kinda technical, so I especially want to stress the summary at the bottom: requiring people check silly little boxes like "Password has a number" and "Password has a punctuation symbol" trains people to pick passwords that are easy to crack, but hard to remember.
A password manager company should know this, and should promote good password choice, perhaps even providing some educational blurbs about how to pick strong, memorable passwords. But Dashlane rejected my extremely strong password, and cited The Handbook of Picking Guessable Passwords that You Won't Remember.
Now, this is not an in-depth review and analysis of Dashlane, and I don't doubt that from a strictly technical perspective, their password manager is quite sturdy. But security as a whole is about the details. Details like human psychology, and how people interact with an app. And Dashlane seriously missed the mark on this one.
I'll be sticking with Passpack for now, as they've always quite happily let me use a strong and memorable password.
Oh, and one more tidbit: Dashlane sponsors How Secure is My Password?, a site which helps you check the security of your password by estimating how long it would hold up under cracking on a low-powered, consumer-grade computer.
Here's how it ranks a password which passes their checkboxes with flying colors: icy!v1trEol

400 years is a horrible score. That password would fall in minutes or seconds on a professional password cracking rig.
Compare with a simplified version of my example password above: Thieves are edified by the iron web.
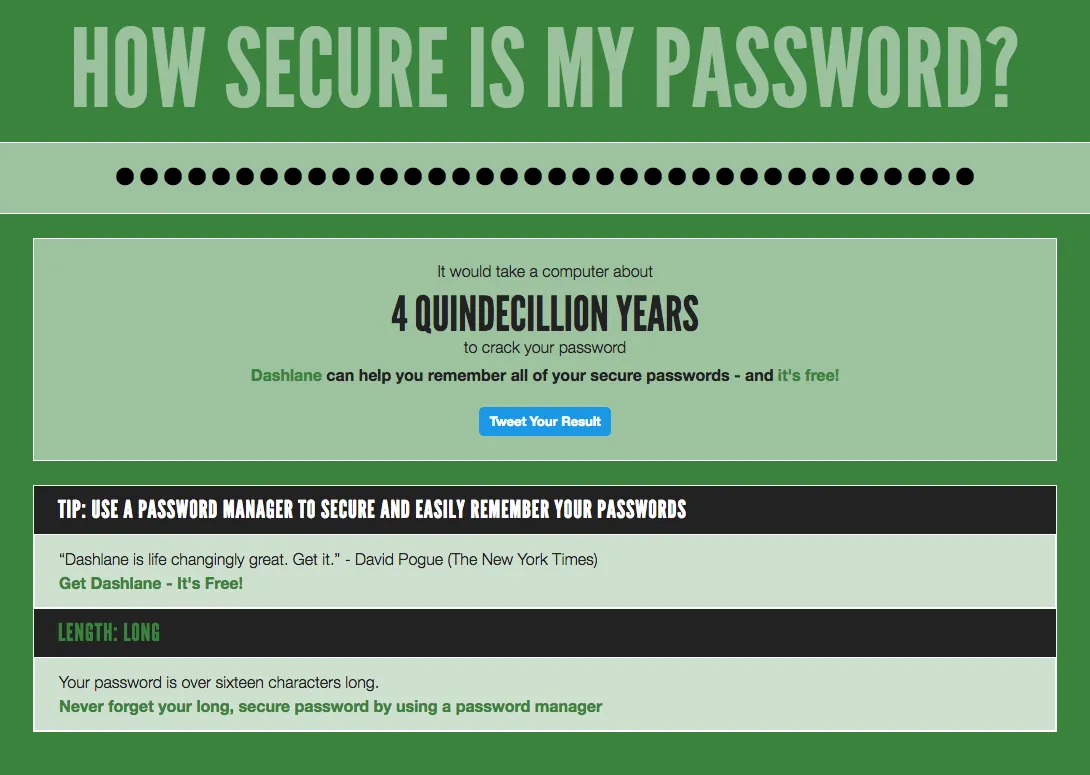
This is a phenomenon I like to refer to as "Missing your own point."
Also be sure and check out PassFault, which is my favorite password strength meter. It's not as pretty or slick as HSIMP, but I think it gives a little bit better analysis, and also breaks down why it scored you how it did so you can tweak and optimize your passwords for maximum durability.
Thanks for reading!

With a background in software development and a passion for security, Nathan has identified blockchain technology as his niche. He is dedicated to creating applications which empower individuals to shape a better world for themselves and others.