The Question
There are several challenges facing intelligence collection efforts. Some of these challenges are addressed in this week’s readings while others can be introduced in our own discussion.
Discussion
What are these challenges?
- Uncertainty – anticipating threat
- Adaption
- Disinformation
- Multi-INT vs all-sources (not having an organizational axe to grind)
- Political use of raw data
Uncertainty as a concept is introduced by Karsner and Zegart (2015), although they don’t seem to focus on it, talking instead in terms of public perception of threat, not in terms of intelligence collection or actual threat. By limiting their discussion to the two major state threats and a third category of “black swan” events, they ignore the dangers of ideology hostile to America and organized crime (in addition, the idea that we need to rely on an international order for our protection has long past it’s “good by” date). By restricting the scope of IR to a myopic view that we are “exceptionally secure”, we cripple our collection efforts before we even put them into play. We, in effect, sleep late on Sunday morning at Pearl Harbor, imagining that there is no possible danger of air attack. We mitigate uncertainty by opening our evaluation of threat to all possibilities.
However, Zegart (2005) does present discussion of another challenge to collection, that of adaption. Following from the idea of uncertainty, once we begin to define and anticipate possible threats, we can adapt our collection (and intelligence overall) efforts accordingly, and hope to reduce the possibility of organizational failure.
Disinformation is a key concept in challenges to collection efforts. Armistead (2004) provides a full discussion of the value of information war in general. Yet, even counterintelligence efforts by “the enemy” do not account for all possible means of disinformation. Sources may lie or misdirect for their own goals. Disinformation may not even be intentional. Duelfer and Dyson (2011) note that Hussein believed that America would not try to force him out of office through a full invasion based upon prior American action towards other regional dictators. On the other hand, we took Hussein's bluff regarding possession of WMD seriously, although he was directing that towards the Iranians (there are several such examples going both ways in this article).
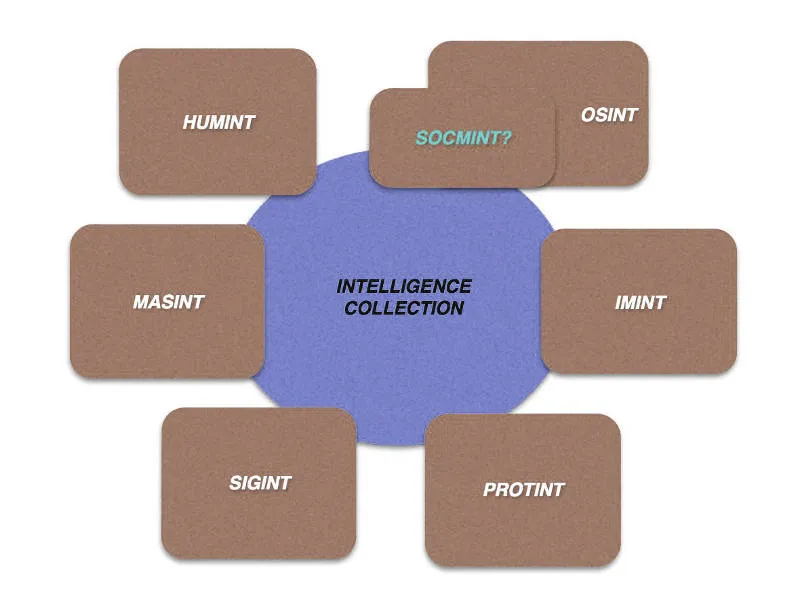
I’m afraid I didn’t fully grasp the scope of the “dispute” between Multi-INT and all-source adherents presented by Lowenthal and Clark (2016). Their summarization of the 5 INT methods seemed to ignore overlapping and/or sub disciplines. However, they address the issue of focusing on each method via it’s stovepipe as the best way to discuss details and core capabilities of each discipline. In addition, they also specify that there ARE people tasked with closing the gaps in, and in integrating the methods.
So I’ll account for the “dispute” they note by referring to the bureaucratic politics as discussed in our Week 1 Lesson Page. I’ll also note that this type of turf battle affects intelligence efforts beyond collection.
Lowenthal and Clark also refer to the issue of raw data. Expanding on their argument, Hulnick (2006) notes that raw data is often provided to policy makers at the same time that it is provided to analysts. And since we know that " some of this raw intelligence may be incomplete, contradictory, or just wrong", something that the IC cannot control is decision-making based on that data.
REFERENCES:
Armistead, L. (2004). Information operations: Warfare and the hard reality of soft power. Potomac Books, Inc.
Duelfer, C. A., & Dyson, S. B. (2011). Chronic Misperception and International Confict:The U.S.-Iraq Experience. International Security, 36(1), 28.
Hulnick, A. S. (2006). What’s wrong with the Intelligence Cycle. Intelligence & National Security, 21(6), 959–979.
Krasner, S., & Zegart, A. (Ed.). (2015). Pragmatic engagement amidst global uncertainty: Three major challenges (p. 57). Stanford, CA: The Hoover Institution.
Lowenthal, M. M., & Clark, R. M. (2015). The Five Disciplines of Intelligence Collection. SAGE.
WEEK 1: Introduction to Collection Lesson Overview. (n.d.).
Zegart, A. B. (2005). September 11 and the adaptation failure of US intelligence agencies. International Security, 29(4), 78–111.
Notes
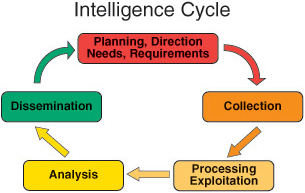
Intelligence collection lies at the core of the Intelligence Cycle. Whether one begins at the Planning and Direction phase of the cycle or at the end with Evaluation and Feedback, intelligence collection efforts drive each phase of the cycle to produce intelligence into a usable product for a decision-maker or warfighter. Intelligence collection has also been an integral part of humanity since antiquity. The ancient Hindu classic, the Arthashastra by Kautilya, describes intelligence collection tradecraft in Book II (Battle of Intrigue) on the use of spies under the use of legitimate cover and as part of covert operations to spread discord amongst the enemy. Sun Tzu’s classic, the Art of War, also makes extensive use of intelligence collection and describes five types of spies.
Since antiquity, intelligence collection has grown infinitely more complex. With the advent of the Industrial Revolution and consequently improvements in technology, the forms of intelligence collection broadened beyond the use of human collectors or human intelligence (HUMINT) to include other forms of intelligence collection disciplines. A clear example was the advent of the hot-air balloon. The French were able to apply this technology and use early balloons for battlefield reconnaissance through the establishment of the Compagnie d'aérostiers, or the Company of aeronauts. These technological trends continue today, but with a more profound implication. The modern-day battlefield is categorized by use of persistent surveillance, precision weapons, and digital command and control systems. This has profound implications for intelligence collection.
++ Krasner, Stephen D. and Amy Zegart. Pragmatic Engagement Amidst Global Uncertainty Three Major Challenges. Stanford, CA: The Hoover Institute, 2015
“THE UNITED STATES IS exceptionally secure. “
ME Points at Amy and Stephen and laughs
“we should be unapologetic about the pursuit of American eco-nomic and security interests “
ME: filed under no shit
they talk about uncertainty in terms of public perception of threat, not in terms of intelligence collection
and the idea that we need to rely on an international order has past it’s “good by” date
++ Lowenthal, Mark and Robert M. Clark. The Five Disciplines of Intelligence Collection. Washington, DC: SAGE Publications, Inc., 2016. (Chapter 1, Pages 1-5).
lists 5 types
OSINT
HUMINT
SIGINT
GEOINT
MASINT
ME: overlap between these ideas
“mystery and myth sorrounding “
TCPED, TPED
Tasking, Collection, Processing, Exploitation, Dissemination
focusing on each mthod via it’s stovepipe; best way to discuss details and core capabilities
there ARE people taksed with closing the gaps in, and in integrating the methods
clandestine (secret but attributable) vs covert (secret and unattirbutable)
collateral = data from outside the stovepipe
multi-INT vs all-sources
raw vs finished
++ Warner, Michael A. Handbook of Intelligence Studies, Edited by Loch K. Johnson. New York: Routledge, 2007. (Chapter 1, Pages 17-27).