
A must! because in the virtual world the online service accounts we use are important assets that must be kept confidential. Because data such as username and password are the main target of cyber criminals.
Just like at home, we keep some valuables such as jewelry, TV, laptop and so on. There was also someone who kept the jewelry in the safe and put it in a locked cabinet for more security. More or less 2-step verification function is the same.
In short, 2-step verification is a kind of 'bulwark' of security enhancements, which requires us to enter a six-digit code after we login to an online account such as Gmail, Yahoo Mail, Facebook, Twitter, Dropbox and other online services. This code will be sent to the phone.
That means if our password is stolen, our account will remain safe. Because the person trying to get into the account we can not can not get the code because it does not hold our phone.
**How 2-step verification works **
Login> Enter username & password> Enter the 6 digit verification code sent to mobile
Yes, it's that simple.
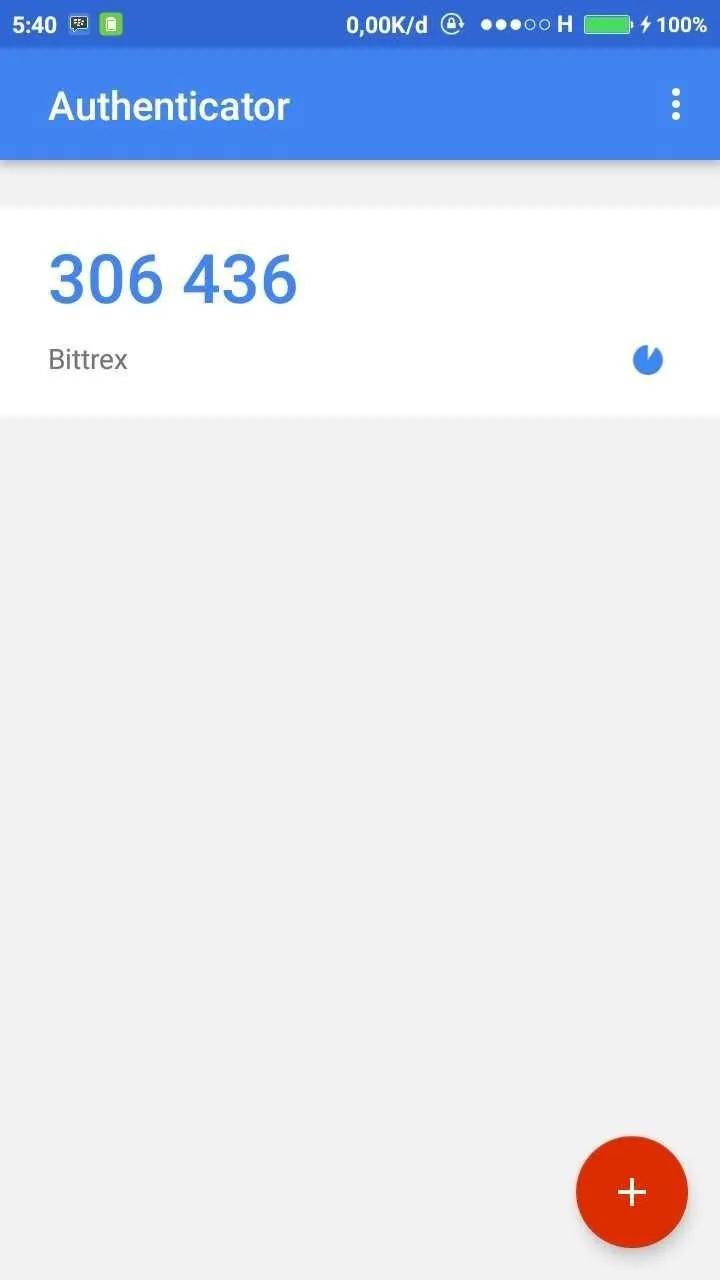
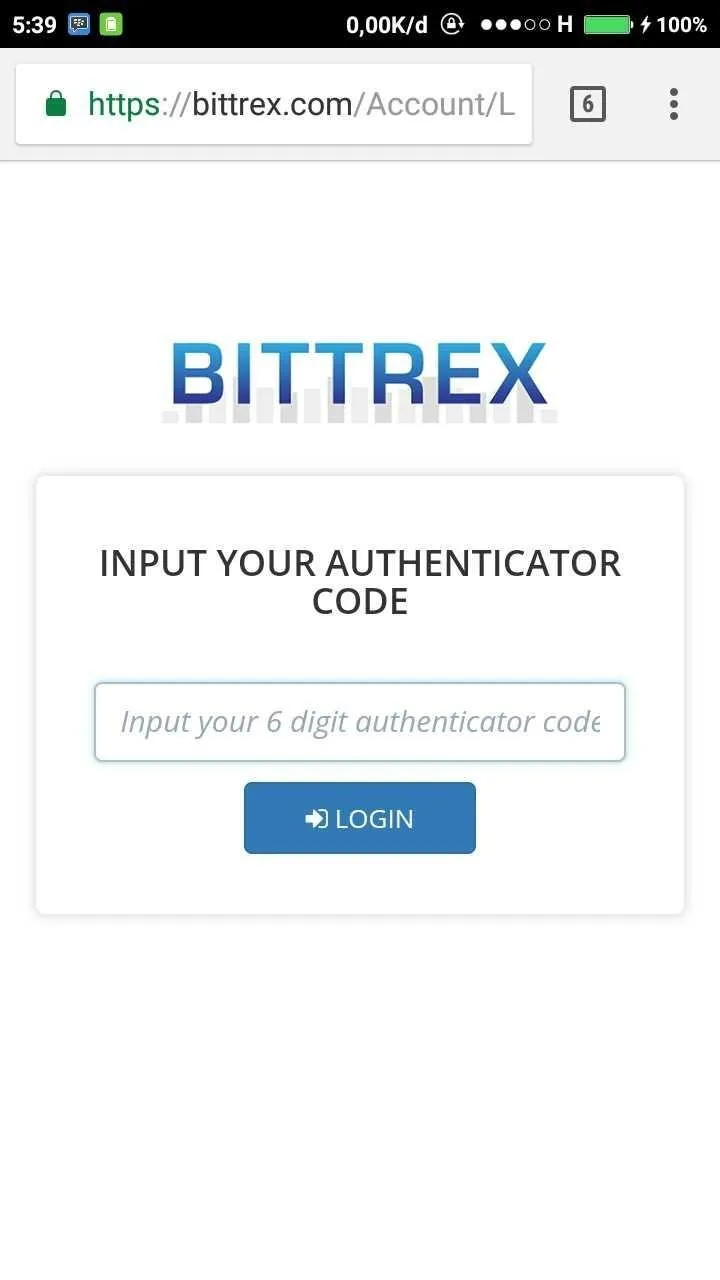
A six-digit verification code can be sent via SMS, or if you're an Android, BlackBerry or iPhone user, you can use an application called Google Authenticator that can generate code. This app works by accessing the Google account on our phone, then scan (scanning) secret barcode on screen by using our camera phone.
The Google Authenticator app for Android does not require an internet connection to work. Even in airplane mode this app can still generate verification codes.
What if our cell phone is lost?
Do not be afraid, when you first turn on the 2-step verification feature, we'll be prompted to provide a backup phone number, which can be used to get a six-digit verification number in case the phone is lost.
We will also be given a set of backup verification codes, which can only be used for login once. If the phone is missing or missed, we can still use this code to login once.
Long passwords are not enough
If you have not enabled the 2-step verification feature on your online accounts, it's time to activate. Because complex and long passwords are not enough to prevent hackers from hacking into our accounts. Logging over an unencrypted Wi-Fi network while using a public hotspot can also be a loophole for hackers to stake out our accounts.
Hackers can also snoop our passwords using keyloggers (a spy program that can record what we type on the keyboard). Or hackers can do social engineering techniques through phishing for users to be deceived and give their identity.
Unfortunately there are still many of us who have not used this 2-step verification feature. Most likely because many who have never heard of it, or have heard but lazy activate it because they have to bother having to login twice.
Source : Konsultasi-cyberlife