Anyone reading this right now, I assume you know or atleast have an idea what metasploit is. If yes, let us quickly look at the tools we will need to set up a test environment. And if you have no idea, kindly bear with me and await my future post blog which would give a comprehensive explanation.
Let's ride on guys!
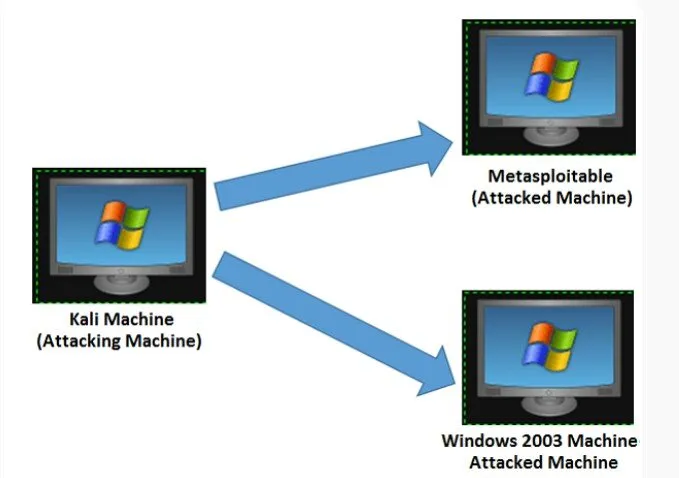
To set up our test environment, we will take the following actions.
- Download and install Virtual box and install it.
- Download and install Kali distribution
- Download and install Metasploitable. We shall use this as our hacking machine.
- Download and install Windows XP ( another hacking machine)
We now have 3 machines in total which will logically be connected to the same network.
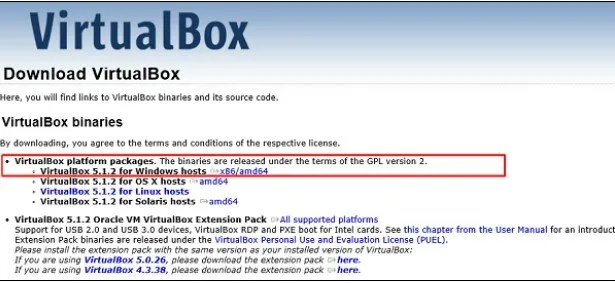
Visit https://virtualbox.org/wiki/Download
Select the version that supports your OS and the hardware configuration of your system.
After you must have selected appropriate version of Virtual Box, the following screen will appear. Click NEXT
Follow the next screen and set location where you want to install the app
You will get a warning message at this point before proceeding with the installation.
Click YES on the screen above which should display the following screen.
Click Install to begin installing the app.
Once the installation is done, the following screen will appear. Click FINISH to exit the set up wizzard.
You will now be greeted with the oepening screen of VirtualBox
Time to install the rest of the hosts for this tutorial.
Visit https://kali.org/downloads/ to download Kali Linux
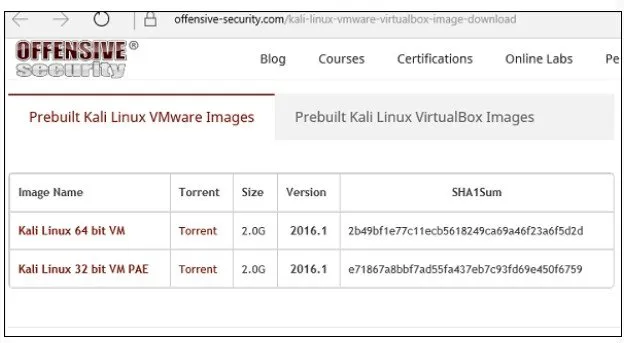
Go to the official website above and download prebuilt Kali Linux VirtualBox images.
Next, open VirtualBox images Manager and go to Machine - NEW
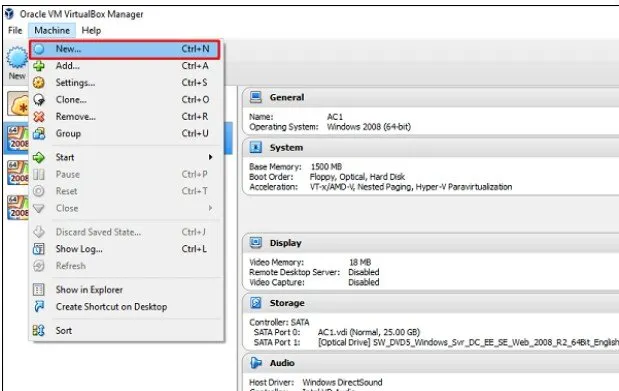
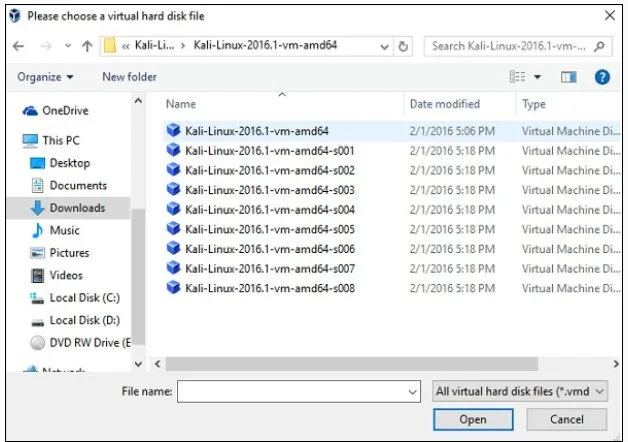
Go to the location where Kali Linux was downloaded and select a virtual hard disk file.
The next screen will prompt you to create a virtual machine. Click the Create button as shown in the screen shot below
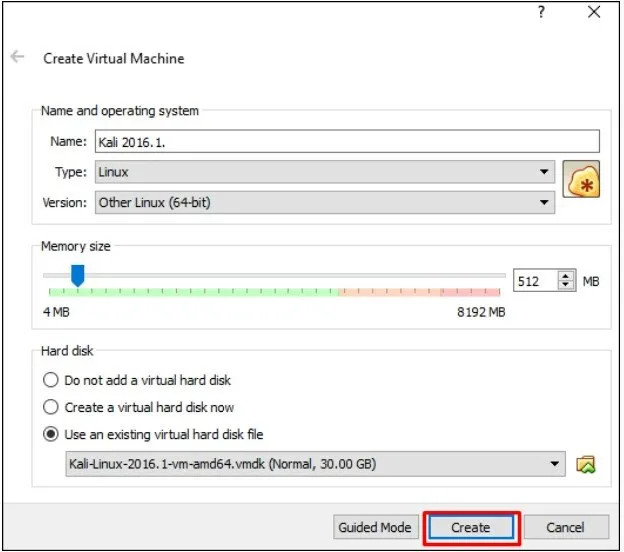
Now You can start Kali OS. Your default username will be root and password will be toor
Posted on Utopian.io - Rewarding Open Source Contributors